0x00 This_is_A_tree
dfs先序遍历树拿到一串看起来像base64的字符串
import os
import queue
class Node:
def __init__(self,path:str,data:str) -> None:
self.path = path
self.data = data
q = queue.Queue()
cur:Node
def dfs(cur:Node):
lpath = cur.path+"/letf/data"
print(cur.data,end='')
if os.path.exists(lpath):
ldata= open(lpath,"r").read()
dfs(Node(cur.path+"/letf",ldata))
rpath = cur.path+"/Right/data"
if os.path.exists(rpath):
rdata = open(rpath,"r").read()
dfs(Node(cur.path+"/Right",rdata))
dfs(Node("./root",open("./root/data","r").read()))
Q2hpbmVzZSB0cmFkaXRpb25hbCBjdWx0dXJlIGlzIGJyb2FkIGFuZCBwcm9mb3VuZCEgU28gSSBXYW50IEdpdmUgWW91IE15IEZsYWcgQnV0IFlvdSBOZWVkIERlY29kZSBJdC5FbmpveSBUaGUgRmxhZyEhOuW4iCDlhZEg5aSNIOaNnyDlt70g6ZyHIOaZiyDlp6Qg5aSn6L+HIOiuvCDlmazll5Eg6ZyHIOaBkiDoioIg6LGrIA==
解码拿到
和buuoj的某题类似,直接在网上找到脚本
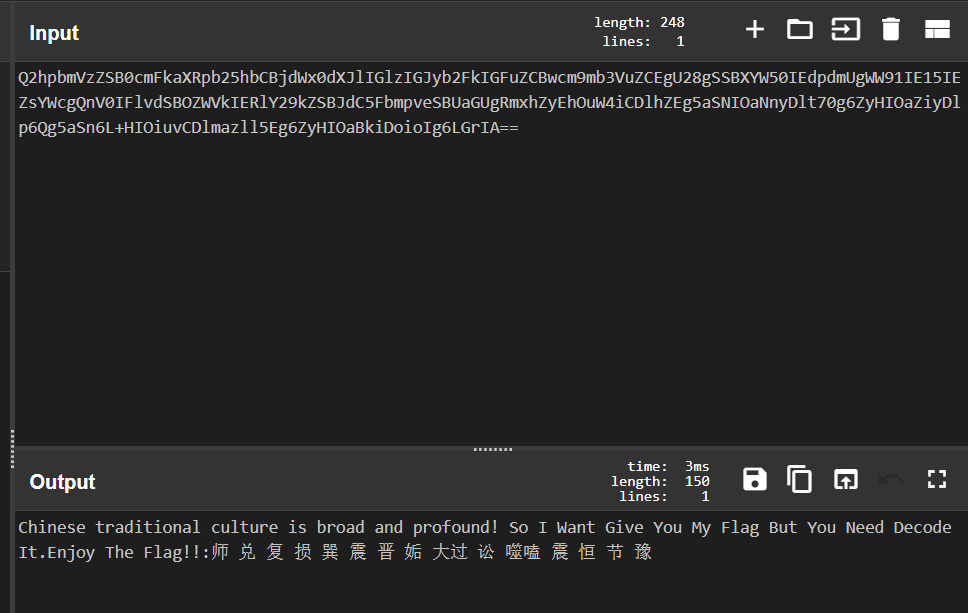
def decrypt4(enc):
temp=''
offset=5
for i in range(len(enc)):
temp+=chr(ord(enc[i])+offset+i)
return temp
def decrypt5(flag):
for a in range(1,200):
enc = ''
for i in flag:
for k in range(200):
if (ord(i) - 97 - 7+26*k)%a==0:
enc+= chr((ord(i) - 97 - 7 + 26 * k) // a + 97)
break
print(enc)
s='师兑复损巽震晋姤大过讼噬嗑震恒节豫'
dic={'坤': '000000', '剥': '000001', '比': '000010', '观': '000011', '豫': '000100', '晋': '000101', '萃': '000110', '否': '000111', '谦': '001000', '艮': '001001', '蹇': '001010', '渐': '001011', '小过': '001100', '旅': '001101', '咸': '001110', '遁': '001111', '师': '010000', '蒙': '010001', '坎': '010010', '涣': '010011', '解': '010100', '未济': '010101', '困': '010110', '讼': '010111', '升': '011000', '蛊': '011001', '井': '011010', '巽': '011011', '恒': '011100', '鼎': '011101', '大过': '011110', '姤': '011111', '复': '100000', '颐': '100001', '屯': '100010', '益': '100011', '震': '100100', '噬嗑': '100101', '随': '100110', '无妄': '100111', '明夷': '101000', '贲': '101001', '既济': '101010', '家人': '101011', '丰': '101100', '离': '101101', '革': '101110', '同人': '101111', '临': '110000', '损': '110001', '节': '110010', '中孚': '110011', '归妹': '110100', '睽': '110101', '兑': '110110', '履': '110111', '泰': '111000', '大畜': '111001', '需': '111010', '小畜': '111011', '大壮': '111100', '大有': '111101', '夬': '111110', '乾': '111111'}
li=[]
k=0
for i in range(len(s)):
if k ==1:
k=0
continue
try:
li.append(dic[s[i]])
except:
t=''
t=t+s[i]+s[i+1]
li.append(dic[t])
k=1
ss=''.join(li)
print(ss)
enc=''
for i in range(0,len(ss),8):
enc+=chr(eval('0b'+ss[i:i+8]))
import base64
print(enc)
x=base64.b64decode(enc).decode()
print(x)
x=decrypt4(x)
x=decrypt5(x)
解得
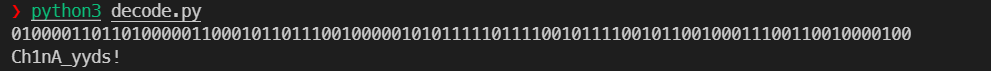
即为flag
0x01 fumo_xor_cli
当时微信公众号发的时候就有了题目想法,就提了缩略图
from PIL import Image
origin = Image.open('TpMSkq.png')
final = Image.new('RGB',(100,133))
_x=0
_y=0
for y in range(1,1190,9):
for x in range(1,893,9):
final.putpixel((_x,_y),origin.getpixel((x,y)))
if(_x%99==0 and _x!=0):
_x=0;
_y=_y+1
else:
_x=_x+1
final.save('key.bmp')
然后我们通过给定的命令行,能提出其中数据的颜色。
我们可以发现其中除了正常的Fumo还有2帧不太正常的帧,
我们把这两个手动提取下,发现图片的size (133,50)
然后我们提的缩略图是100x133
import re
from PIL import Image
result=[]
r=[]
g=[]
b=[]
file=open('data.txt','r').read()
res=re.findall("\[(.*?)[ESC]",file)
print(len(res))
print(len(res))
for i in res:
tmp=i.split(";")
r.append(tmp[2])
g.append(tmp[3])
b.append(tmp[4][:-2])
flag=Image.new(mode='RGB',size=(100,133),color=(0,0,0))
file=open('part2.txt','r').read()
res=re.findall("\[(.*?)?",file)
print(len(res))
print(len(res))
for i in res:
tmp=i.split(";")
r.append(tmp[2])
g.append(tmp[3])
b.append(tmp[4][:-2])
tot=0
for i in range(0,100):
for j in range(0,133):
flag.putpixel((i,j),(int(r[tot]),int(g[tot]),int(b[tot])))
tot+=1
print(flag.size)
flag.save('ano.png')
然后xor一下就出flag了
0x02 easydsp
数字信号处理。通过数字信号恢复音频
import wave
import struct
f1 = open('data1.txt').read()
f2 = open('data2.txt').read()
f3 = open('data3.txt').read()
f4 = open('data4.txt').read()
data1 = [float(line) for line in f1.splitlines()]
data2 = [float(line) for line in f2.splitlines()]
data3 = [float(line) for line in f3.splitlines()]
data4 = [float(line) for line in f4.splitlines()]
count = len(data1)
data_all = [data1[i] + data2[i] + data3[i] + data4[i] for i in range(count)]
data_3_4 = [data1[i]-data2[i] for i in range(count)]
def to_wav(file, data):
nchannels = 1
sampwidth = 2
second = 5
sampling_rate = count // second
nframes = count
amplitude = 1900
wav_file = wave.open(file, 'w')
wav_file.setparams((nchannels, sampwidth, int(sampling_rate), nframes, 'NONE', 'not compressed'))
for i in data:
wav_file.writeframes(struct.pack('h', int(i * amplitude)))
to_wav('1-2.wav',data_3_4)
得到的音频就有了相关的波形图,而且去除了噪点,利用1-2的这个频谱。
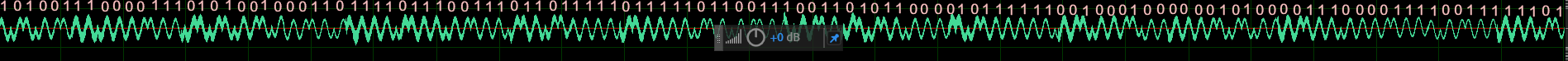
手动读下flag就可以了 类似曼彻斯特?
0x03 low_re
测信道攻击,通过枚举每一位的字符同时检测指令数目来找flag。
利用pintools 手动逐位爆破。
from subprocess import Popen, PIPE
from sys import argv
import string
import pdb
from multiprocessing import Process, Value, Manager
from time import ctime, sleep
from tqdm import tqdm
from ctypes import c_char_p
import random
import sys
pinPath = ".\pin.exe"
pinInit = lambda tool, elf: Popen([pinPath, '-t', tool, '--', elf], stdin=PIPE, stdout=PIPE)
alpha = []
for i in range(32, 128):
alpha.append(chr(i))
def find(start, end):
for i in range(start, end):
print(i)
pin = pinInit(".\\obj-intel64\\icount.dll", ".\low_re.exe")
result = 'S1deCh4nnelAtt@ck'.format(alpha[i])
pin.stdin.write('S1deCh4nnelAtt@ck'.format(alpha[i]).encode('utf-8'))
print(pin.communicate()[0].decode() + ":" + result)
def multi_work(iter_function, totalProcess=10, lenList=96, base=0):
gap = lenList // totalProcess
process_list = []
print("Totally %d processes" % totalProcess)
for i in range(totalProcess):
process = Process(target=iter_function, args=(base + i * gap, base + (i + 1) * gap))
process.start()
process_list.append(process)
for t in process_list:
t.join()
print("Exiting Main Process")
if __name__ == '__main__':
multi_work(find)
0x04 in_the_vaporwaves
挺无语的题,好好看看频谱图就行了,能看到摩斯

SCTFDES1R3_DRIVES_INT0_VAPORW@VES
0x05 August 10, 2021
Poly network的题,挺简单的
找一个哈希加参数 和 payforflag()哈希一样就完了,
"""
[+] contract address: 0xa9Ac4071925Ef7cDAC46B2FcbD3afF86A5b4fa32
[+] transaction hash: 0xf298c8b32451fe71c999594b634db485fa543a77d04ef1deb9a48caa718d2de8
"""
import web3
from web3 import Web3,HTTPProvider
from web3.auto import w3
import hashlib
import json
from Crypto.Util.number import *
web3=Web3(HTTPProvider("http://124.71.147.175:8545/"))
print(web3.isConnected())
"""key=web3.eth.account.create()
print(key.address)
print(hex(bytes_to_long(key.privateKey)))"""
acct= web3.eth.account.from_key('0x719e289ff8306c4e9ff66476bf35889e24eaa475c80878a2a42c760efaed2134')
print(acct.address)
def get_txn(src, dst, datad,nonce, value=0, ):
return {
"from": src,
"to": dst,
"gasPrice": web3.toWei(1,'gwei'),
"gas": 3000000,
"value": web3.toWei(value,'wei'),
"nonce": nonce,#web3.eth.getTransactionCount(src),
"data": datad,
"chainId": 7486
}
print(web3.eth.getCode("0xAe7dd2aAc652b3492326dB135D48844A8e08833a"))
to_addr="0xAe7dd2aAc652b3492326dB135D48844A8e08833a"
data=long_to_bytes(0x66fbe3940000000000000000000000000000000000000000000000000000000000000020000000000000000000000000000000000000000000000000000000000000001766756e6338363533393536353435393638393131313830000000000000000000).decode('utf-8')
nonce=web3.eth.getTransactionCount(acct.address)
signed_txn = web3.eth.account.signTransaction(get_txn(src=acct.address, dst=to_addr, datad=data, nonce=nonce), acct.privateKey)
txn_hash = web3.eth.sendRawTransaction(signed_txn.rawTransaction).hex()
print(txn_hash)
print(web3.eth.getTransactionReceipt("0xe4ff900301a55ae0e9b486c3add1aea4151d72f63055ecbe771c1bbd450a62d8"))
0x06 Constructor?
预编译合约,然后部署一个有initcode的合约就行了。同时爆破create2满足地址大小就行了。
"""
[+] contract address: 0xe8AB319dBCe2A2467e393FB6EA98A8A30e4974ac
[+] transaction hash: 0xe93e4fdd0d590f68bd186fad693f923470f32ebcf3b080dd0f787baba2214adb
"""
import web3
from eth_abi import encode_abi
from web3 import Web3,HTTPProvider
from web3.auto import w3
import hashlib
import json
from Crypto.Util.number import *
web3=Web3(HTTPProvider("http://124.71.147.229:8545/"))
print(web3.isConnected())
#print(hex(bytes_to_long(web3.eth.account.create().key)))
acct= web3.eth.account.from_key('0x719e289ff8306c4e9ff66476bf35889e24eaa475c80878a2a42c760efaed2134')
print(acct.address)
abi=[
{
"inputs": [],
"name": "changesuccess",
"outputs": [],
"stateMutability": "payable",
"type": "function"
},
{
"inputs": [],
"name": "isSolved",
"outputs": [
{
"internalType": "bool",
"name": "",
"type": "bool"
}
],
"stateMutability": "nonpayable",
"type": "function"
},
{
"inputs": [],
"name": "payforflag",
"outputs": [],
"stateMutability": "payable",
"type": "function"
},
{
"inputs": [
{
"internalType": "address",
"name": "a",
"type": "address"
},
{
"internalType": "bytes",
"name": "message",
"type": "bytes"
},
{
"internalType": "bytes32",
"name": "salt",
"type": "bytes32"
}
],
"name": "registContract",
"outputs": [],
"stateMutability": "nonpayable",
"type": "function"
},
{
"inputs": [],
"name": "success",
"outputs": [
{
"internalType": "bool",
"name": "",
"type": "bool"
}
],
"stateMutability": "view",
"type": "function"
},
{
"inputs": [
{
"internalType": "address",
"name": "",
"type": "address"
}
],
"name": "target",
"outputs": [
{
"internalType": "address",
"name": "",
"type": "address"
}
],
"stateMutability": "view",
"type": "function"
},
{
"inputs": [],
"name": "value",
"outputs": [
{
"internalType": "uint256",
"name": "",
"type": "uint256"
}
],
"stateMutability": "view",
"type": "function"
}
]
def get_txn(src, dst, datad,nonce, value=0, ):
return {
"from": src,
"to": dst,
"gasPrice": web3.toWei(1,'gwei'),
"gas": 5000000,
"value": web3.toWei(value,'wei'),
"nonce": nonce,#web3.eth.getTransactionCount(src),
"data": datad,
"chainId": 4047
}
to_addr="0xa9Ac4071925Ef7cDAC46B2FcbD3afF86A5b4fa32"
"""
print(web3.toHex(web3.eth.getCode("0x9a5e63fF1cb8bDEaaD09B91d6aAd78EAeA8ac7Fc")))
print('0x'+'2'.rjust(40,'0'))
print('0x'+hex(1708)[2:].rjust(64,'0'))"""
"""
0x0000000000000000000000000000000000000002
0x6080604052348015600f57600080fd5b50608d8061001e6000396000f3fe608060405260043610601c5760003560e01c80630b93381b14602b575b6000805460ff19166001179055005b348015603657600080fd5b5060005460439060ff1681565b604051901515815260200160405180910390f3fea2646970667358221220b0621c248d6d6606cdee76393ad84c4a0e49db57f0f6737aa40d4e36c80ad36764736f6c63430008070033
0x0000000000000000000000000000000000000000000000000000000000001f95
"""
param = encode_abi(['uint256','bytes','bytes32'],[2,bytes.fromhex('6080604052348015600f57600080fd5b50608d8061001e6000396000f3fe608060405260043610601c5760003560e01c80630b93381b14602b575b6000805460ff19166001179055005b348015603657600080fd5b5060005460439060ff1681565b604051901515815260200160405180910390f3fea2646970667358221220b0621c248d6d6606cdee76393ad84c4a0e49db57f0f6737aa40d4e36c80ad36764736f6c63430008070033'),(21943).to_bytes(32,'big')])
sel=web3.keccak(b'payforflag()')[:4]
data=sel
#off=bytes_to_long(web3.sha3(1+int(acct.address,16)))
#a=web3.eth.getStorageAt(to_addr,web3.keccak(bytes.fromhex(acct.address[2:]).rjust(0x20,b'\x00')+b'\x01'.rjust(0x20,b'\x00')))
#print(a)
nonce=web3.eth.getTransactionCount(acct.address)
signed_txn = web3.eth.account.signTransaction(get_txn(src=acct.address, dst=to_addr, datad=data, nonce=nonce), acct.privateKey)
txn_hash = web3.eth.sendRawTransaction(signed_txn.rawTransaction).hex()
print(txn_hash)
import time
time.sleep(6)
print(web3.eth.getTransactionReceipt(txn_hash))
"""
#print(web3.eth.getTransactionReceipt('0x875ea75d80facfa204a8eab364d3ad62e3aefb7fd40d51d43807d390b66d9e44'))
print(web3.eth.getTransactionReceipt("0x35fd89b5db12d05c8b7b2c7daf1d62d9aeee7b5ae560cf077d80560ef676a270"))
0x1bdDCdA2d1914Fb966237f32df6db10BB3fC3983
0x0000000000000000000000000000000000000002
0x000000000000000000000000000000000000000000000000000000000001f86e
1:ID 0x0a097d23302549b21522b538582094b4a81dbc074c5a7fe912f9d215a6eb95cf
2:Success 0xbbca32c6c50b2626e870ade268446f3ad8869bd55b1e2bf09aa38784da01fbe2
"""
"""
0x00a26019000000000000000000000000000000000000000000000000000000000000000200000000000000000000000000000000000000000000000000000000000000600000000000000000000000000000000000000000000000000000000000022dc8000000000000000000000000000000000000000000000000000000000000017d60806040526ec097ce7bc90715b34b9f100000000060025534801561002357600080fd5b5061014a806100336000396000f3fe6080604052600436106100345760003560e01c80630b93381b146100435780633fa4f24514610072578063dad9da8a14610096575b6000805460ff19166001179055005b34801561004f57600080fd5b5060005461005d9060ff1681565b60405190151581526020015b60405180910390f35b34801561007e57600080fd5b5061008860025481565b604051908152602001610069565b3480156100a257600080fd5b506100cc6100b13660046100e4565b6001602052600090815260409020546001600160a01b031681565b6040516001600160a01b039091168152602001610069565b6000602082840312156100f657600080fd5b81356001600160a01b038116811461010d57600080fd5b939250505056fea26469706673582212206638ed3ef45ec249654b9bed501130379b5680408c7e503ba5b9110568e7b79e64736f6c63430008070033000000
"""
 跳跳糖
跳跳糖
